SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
Contact UsExplaining cloud security infrastructure by way of Tetris.

Cloud infrastructure might best be compared to the game Tetris by orchestrating the use of a variety of structured building blocks mixed with the elasticity of “silly putty” for constructing an organization’s data processing needs. One of the biggest drivers for the movement to the cloud is to reduce the need for a significant investment in development & infrastructure, so many organizations are choosing to buy versus build their infrastructure, avoiding much of the administrative overhead with an on-premise solution.
Additionally, many organizations are empowered by adopting cloud infrastructure so they can rapidly bring new capabilities to market with a flexible and scalable platform for storing, managing, and accessing data via applications over the Internet. In this blog post, we’ll discuss the inner workings of cloud infrastructure, discovering its key components, benefits, and its value to various industries.
Cloud infrastructure encompasses many of the same components or services organizations are accustomed to in their on-premises data center, including, but not limited to:
These combined components are the foundation which several cloud service providers offer as a product known as the infrastructure as a service (IaaS) cloud computing model. A very popular approach for many organizations is to “lift and shift” their on-premise solutions by migrating their applications, infrastructure, and associated data to the cloud with minimal or no changes – leveraging the IaaS (infrastructure as a service) cloud computing model. The key difference is now the cloud service provider is primarily responsible for maintaining and optimizing these robust and flexible components for your organizational benefit. Another key difference for most consumers and relevant from a security perspective is a shared cloud infrastructure, such as the storage, compute, and networking capabilities which are shared by multiple customers.
Cloud infrastructure enables organizations to quickly scale their computing resources up or down, providing the elasticity to meet their business needs. This scalability of infrastructure offered by cloud service providers promises efficient resource utilization, budgetary optimization, and increased agility. Both vertical scaling, the concept of adding/removing resources to an existing virtual machine and horizontal scaling, the method for increasing/decreasing the number of virtual machines in a resource pool, are commonly used across the various providers (see Figures 1 and 2). Additionally, when well architected, cloud infrastructure offers reliability through highly available and fault tolerant systems, minimizing downtime and increased uptime for service availability across the cloud service provider’s availability zones and regions. Most importantly, the security components offered can provide strong security controls, including data encryption, access controls, backup & recovery mechanisms, enhancing data protection and compliance.
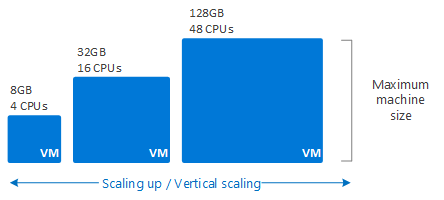
Figure 1. Vertical Scaling1
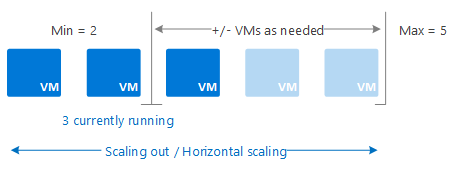
Figure 2. Horizontal Scaling1
Cloud infrastructure can be categorized into three main types: public, private, and hybrid. Public cloud infrastructure is a managed service provided by third-party cloud service providers (i.e., AWS, Azure, and GCP) where consumers can subscribe to offerings, utilizing a shared infrastructure, and typically connecting to the resources over the Internet. Private cloud infrastructure is a dedicated environment usually for a single organization using on-premise equipment allowing for enhanced control and security over their sensitive data often to accommodate regulatory requirements. Hybrid cloud infrastructure blends the characteristics of both public and private clouds, permitting organizations to take advantage of the benefits of both models.
With any number of components inside cloud infrastructure, organizations can architect and construct a wide variety of systems. One of the most common use cases is the deployment of web applications, using load balancing to assist with fault tolerance, and some type of backend database for storing sensitive information. Here are a few examples that demonstrate the orchestration of many of the cloud infrastructure components from Azure, AWS, and GCP to further illustrate this common scenario.
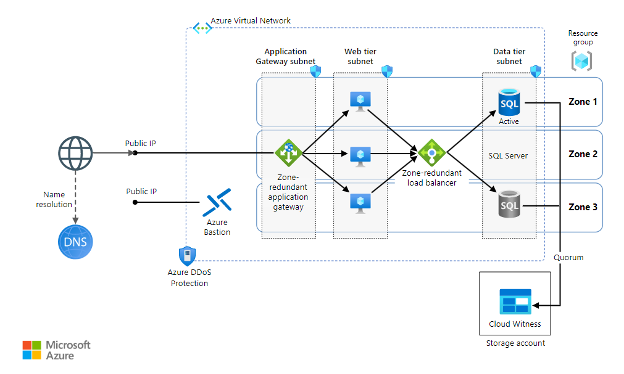
Azure: Web application with Relational database2
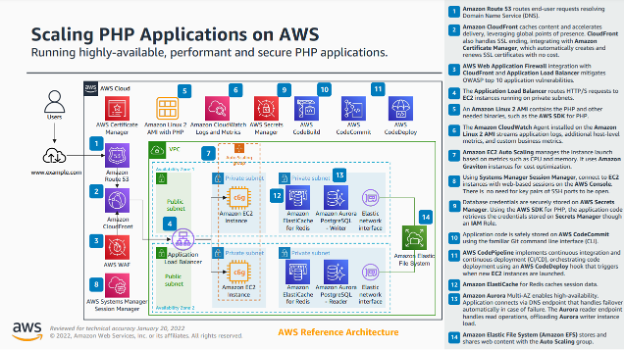
AWS: Highly Available PHP Application3
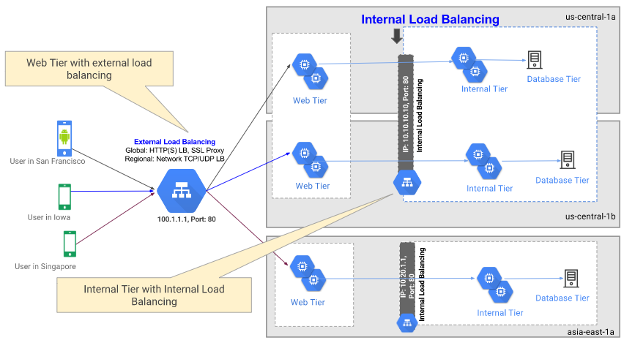
GCP: Load Balancing4
Overall, cloud infrastructure is the backbone for business activities and data processing, providing organizations with the agility, scalability, resiliency, and cost efficiency necessary to flourish. A well architecture cloud environment, utilizing the components of cloud infrastructure, permits the organization to focus on their business objectives while transferring many of the complex tasks of cloud infrastructure management to the cloud service providers. Learn more about cloud infrastructure and the relationship with security practices from SANS courses at https://www.sans.org/cloud-security/.
ABOUT THE AUTHOR
Chris Edmundson has been employed in the information technology arena for over 25 years, working in a wide variety of roles, primarily in the public sector related to administration of K-12 public schools and at higher education institutions. He currently manages the Security Operations for the Office of Information Technology at the University of Colorado Denver | Anschutz Medical Campus. Chris is an Associate Instructor teaching SEC488: Cloud Security Essentials. Read more about Chris here.
REFERENCES:
[1] https://learn.microsoft.com/en-us/azure/azure-monitor/autoscale/autoscale-overview
[2] https://learn.microsoft.com/en-us/azure/architecture/high-availability/ref-arch-iaas-web-and-db
[4] https://cloud.google.com/architecture/scalable-and-resilient-apps


Chris Edmundson has been employed in the information technology arena for over 25 years, working in a wide variety of roles, primarily in the public sector related to administration of K-12 public schools and at higher education institutions.
Read more about Chris Edmundson