SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
Contact Us
Are you familiar with the Konami code? The one popularized by the Contra video game?

Pictured above: Tangentially related to SSH
If not, let me fill you in. This code is a sequence of control actions for some video games that'll let you jump forward in the game (some call it a "cheat," but I'd rather not judge.). The code itself is a series of button presses as follows (from Wikipedia):

For me, learning about SSH control sequences felt like finding SSH's Konami code. First I learned how to kill an SSH client that wasn't responsive, which was convenient. Then, finding out about changing SSH's options *after I had established the connection* felt like cheating. Adding SOCKS proxies or local and remote port forwards after I've already connected to an SSH server is very useful, and far less annoying than typing my SSH key passphrase again.
So, how do you start a control sequence? First, make sure "Enter" was the last key you pressed, as the SSH client won't notice the control sequence otherwise. Next, press the tilde character (shift + backtick) followed by another character.
What are the support escape sequences, you ask? Well, press "?" as your second character, and your SSH client will tell you:
Supported escape sequences:
Of these, I use "~." to kill stubborn SSH clients, "~C" to use additional SSH options (like "-D 8080" to start up a new SOCKS proxy), and rarely "~#" to see what forwards I've created.
Here's an example of me connecting to an SSH server (I set up the alias in my ~/.ssh/config file) and using an SSH control sequence to add a SOCKS proxy on port 9001 retroactively:
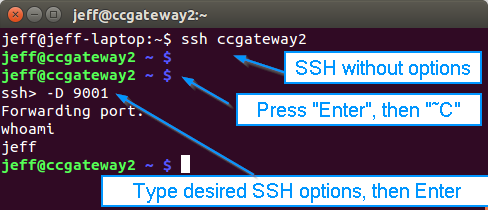
An example of using an SSH escape sequence
Note the line beginning with "whoami". We were interacting with the SSH client itself at the line beginning with "ssh>", but when we finished that by pressing Enter, we didn't get a new prompt from the remote server. The input was still accepted, though, which is why the "whoami" command I typed returned "jeff" in the next line, followed by another newline and the SSH server's prompt. Gosh, this is useful stuff.
Thanks for reading along! I hope you find as much use for the SSH Konami Code as I have.
- Jeff McJunkin Follow @jeffmcjunkin


Jeff McJunkin, Rogue Valley InfoSec founder, has led Fortune 100 pen tests and shaped Core NetWars. His key role in SANS Holiday Hack Challenge and hands-on security innovations continue to elevate the industry, advancing defenses worldwide.
Read more about Jeff McJunkin