SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
Contact UsSmishing attacks can take many forms. In this blog, learn how to avoid being tricked.
If you’re like most everyone with a personal device, you’ve seen a significant uptick in the number of SMS messages, with too many not pertinent to your life. On occasion, these could be wrong numbers that we can chalk up to honest mistakes or “fat fingers.” But more frequently, these represent an increasingly common type of attack referred to as smishing. To understand smishing, we must first understand SMS messaging.
What is SMS?
SMS, more commonly known as texting, stands for Short Message Service and is a means of sending short messages to mobile devices, to include cell phones and smart phones.
Ok, so, what is smishing?
Smishing is a type of social engineering phishing attack using SMS. Think of smishing as a combination of phishing and SMS. Similar to phishing scams, smishing messages typically include a threat, enticement, and even curiosity to click a link or call a number, often with the goal of getting you to hand over sensitive information.
The FCC (Federal Communications Commission) recently published a warning on the rising threat of smishing attacks, attacks aimed at stealing personal information and/or for financial gain and scams. The alert published by the FCC reads:
“The FCC’s Robocall Response Team is alerting consumers to the rising threat of robotexts. Substantial increases in consumer complaints to the FCC, reports by non-government robocall and robotext blocking services, and anecdotal and news reporting make it clear that text messages are increasingly being used by scammers to target American consumers.”
Smishing attacks can take many forms. Sometimes they can leverage the “wrong number” trick to elicit a mistaken click:
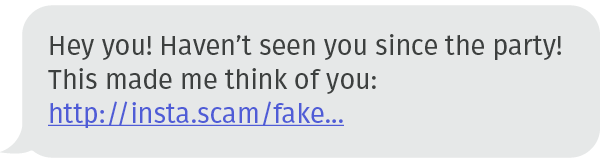
Or, sometimes, they pander to more basic instincts with the promise of cash rewards:
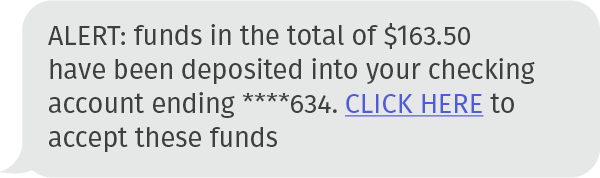
If you are in the United States, the current time is ripe for an increase in a different type of SMS attacks: the political donation scam.
Remember, hackers read the news too, and are very aware of upcoming and trending events. As we approach the midterm elections of November 2022, political campaigns become increasingly prominent, newsworthy, and a focus for many. Hackers know this and use SMS to feed on our fears and desires for the future. Utilizing SMS as a social engineering tool, hackers tempt us to be vulnerable and comment on many topics important to us: campaign promises related to health care and education, other candidates from opposing parties, job and market future outlook, and even campaign rallies and fundraising requests. You can imagine how a few of these attempts might prompt a recipient to inappropriately react and put themselves at risk:
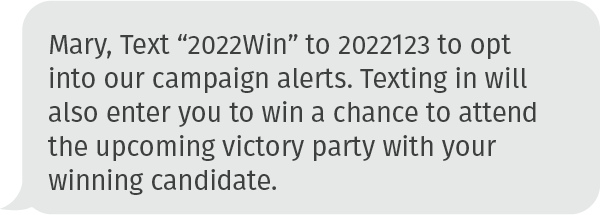

Because politicians can and do use SMS messaging as a campaign tool, we are primed to view a text from an unknown number with less scrutiny. This means attacks like these can be especially effective.
Help protect yourself and your personal information against SMS attacks with the following quick tips:
Resources:
Cheryl Conley is a phishing and security awareness SME, with the CISSP (Certified Information Systems Security Professional) and SSAP (SANS Security Awareness Professional (SSAP) certifications, along with a Master’s degree specializing in Information Security.
Read more about Cheryl Conley