SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
Contact UsWe were recently the unlucky recipients of what we describe as a "gap spam" scheme on the SANS DFIR mailing list. Here's how we stopped it.

We recently responded to an unusual and particularly wily problem on the SANS DFIR mailing list. This list, with nearly 7,000 members, is used for exchanging all manners of digital forensic and incident response information, and is a great resource for the DFIR community. However, several weeks ago, we found that anyone sending a message to the list almost immediately received what looked like a “response” containing spam.
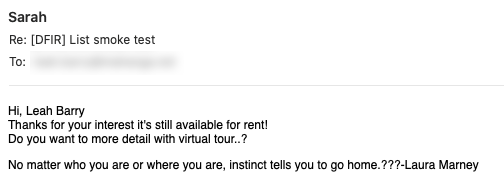
Unfortunately, spam occasionally happens with list members. Normally, we just look up the sender of the spam message and remove them from the list. However, these messages were from senders that were not list members.
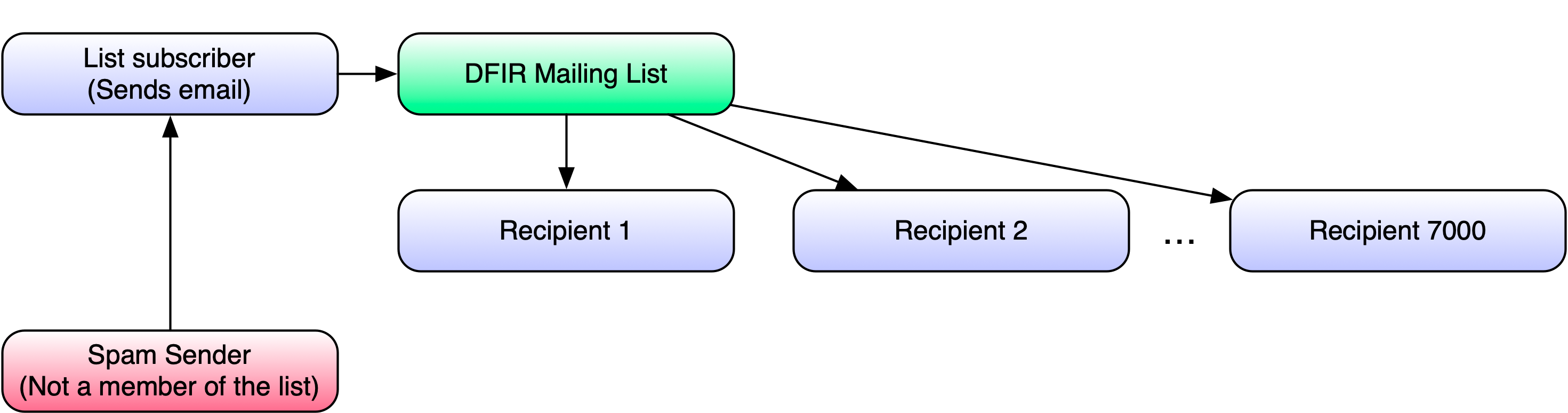
It was clear that at least one recipient address was being used to harvest messages and forge the “replies”. Finding the one or two bad actors from a list of 7,000 was going to prove difficult. We entertained the idea of forcing all members to revalidate, and several other options, but all were either extremely labor-intensive or highly intrusive to list members. I inquired about this with some of the SANS Support Team, and Donald Endersby suggested some form of a mail merge. We would send individual messages to list members, each containing some form of a unique identifier, then track which identifier(s) garnered a response. It seemed simple enough, but the only tie between a legitimate sender and the corresponding spam “response” was the sender’s email address. This solution immediately became much more complex.
After a little virtual whiteboard work, we came up with an enacted the following solution:
cat fakenamegenerator.csv | awk '{OFS=""; print $1," ",$2," <",tolower($1),".",tolower($2),"@mahanga.net>"}' > fake_senders.txt
./mailman-subscribers.py -o recipients.txt -v -r -f $HOSTNAME $LISTNAME $PASSWORDpaste fake_senders.txt list_recipients.txt | sed 's/> />,/' > remailer_pairs.txtX-Original-To: $RECIPIENT
X-Original-To: dfir@lists.sans.org
Delivered-To: dfir@lists.sans.org
To: dfir@lists.sans.org
X-BeenThere: dfir@lists.sans.org
X-Mailman-Version: 2.1.20
Precedence: list
List-Id: "Incident-Response, Malware Analysis,
Digital Forensics Professionals in the SANS Community"
<dfir.lists.sans.org>
List-Unsubscribe: <https://lists.sans.org/mailman/options/dfir>,
<mailto:dfir-request@lists.sans.org?subject=unsubscribe>
List-Archive: <https://lists.sans.org/mailman/private/dfir/>
List-Post: <mailto:dfir@lists.sans.org>
List-Help: <mailto:dfir-request@lists.sans.org?subject=help>
List-Subscribe: <https://lists.sans.org/mailman/listinfo/dfir>,
<mailto:dfir-request@lists.sans.org?subject=subscribe>
Errors-To: dfir-bounces@lists.sans.org
Sender: "DFIR" <dfir-bounces@lists.sans.org>
Subject: [DFIR] List smoke test
Reply-To: test.controller@mahanga.net
From: $SENDER
Hello to the DFIR list. We're running a smoke test right now, so please pardon the interruption. We're eager to report our findings soon - so look for the blog post!!
No need to reply to this message. Thanks for your understanding and cooperation.
-$FIRSTNAMEcat remailer_tuples.txt | while IFS=, read SENDER RECIPIENT FIRSTNAME; do
RECIP_EMAIL=$( echo -n $RECIPIENT | sed -e 's/.*<\(.*\)>/\1/' )
echo "$SENDER -> $RECIPIENT"
cat mail_template.txt | sed "s/\$SENDER/$SENDER/" | sed "s/\$RECIPIENT/$RECIPIENT/" | sed "s/\$FIRSTNAME/$FIRSTNAME/" | sendmail $RECIP_EMAIL
doneIt took a grand total of one minute before we’d found the culprit. They were immediately removed from the list. To our surprise, another one was discovered several minutes later - and was promptly removed from the list as well.
All in all, this was an unexpected but interesting drill. I’m not sure if this “gap spam” approach is common with any other mailing lists, but this is one approach that can help if you encounter such tactics.


Launched in 1989 as a cooperative for information security thought leadership, it is SANS’ ongoing mission to empower cyber security professionals with the practical skills and knowledge they need to make our world a safer place.
Read more about SANS Institute