SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
Contact UsHere is our suggested Course Roadmap to guide you in your search for training. Use the Job Role Matrix to match a course with common job roles in DFIR
Whether you're seeking to maintain a trail of evidence on host or network systems or hunting for threats using similar techniques, larger organizations need specialized professionals who can move beyond first-response incident handling to analyze an attack and develop an appropriate remediation and recovery plan. Our DFIR Curriculum will teach you how to detect compromised systems, identify how and when a breach occurred, understand what attackers took or changed, and successfully contain and remediate incidents.
DFIR Course Roadmap
Here is our suggested DFIR Course Roadmap to guide you in your search for training. This is just a recommendation, and all courses can be taken in different order. However, some courses might skip over introductory and intermediate concepts so make sure you look at the pre-requisites of the course you are interested in, before hand. Click on the image to see the full SANS Roadmap.

SANS DFIR Essential Courses
More than half of jobs in the modern world use a computer. Most people aged 18-30 are 'digitally fluent'; accustomed to using smartphones, smart TVs, tablets, and home assistants, in addition to laptops and computers, simply as part of everyday life. Yet, how many of these users understand what's going on under the hood? Do you want to know more about Digital Forensics and Incident Response? If you answered 'yes' then these courses are for you!
FOR498: Battlefield Forensics & Data Acquisition | GBFA: With digital forensic acquisitions, you will typically have only one chance to collect data properly. With this course you will learn to respond, identify, collect, and preserve data no matter where that data hides or resides. This course will teach you to:
“FOR498 provided information I can take back to my company and begin using immediately. It will be very easy to show leadership the ROI on this course." - Jennifer Welsh, CNO Financial Group |
SANS DFIR Endpoint Forensics Courses
The SANS Endpoint & Network Forensics courses provide you with the “must-have” skills any forensic & incident response professional should have. Whether you are seeking a trial of evidence oh host or network systems, larger organizations need specialized professionals who can move beyond-first response incident handling to analyze an attack and develop an appropriate remediation and recovery plan. These courses will help you with the skills needed to be that specialized professional!
FOR500: Windows Forensic Analysis | GCFE: All organizations must prepare for cybercrime occurring on computer systems and within corporate networks. Demand has never been greater for analysts who can investigate crimes such as fraud, insider threats, industrial espionage, employee misuse, and computer intrusions. This course will teach you to:
|
FOR508: Advanced Incident Response, Threat Hunting, and Digital Forensics | GCFA: The course uses a hands-on enterprise intrusion lab -- modeled after a real-world targeted attack on an enterprise network and based on advanced threat actor tactics -- to lead you to challenges and solutions via extensive use of the SIFT Workstation and best-of-breed investigative tools. The course will teach you to:
“FOR508 exceeded my expectations in every way. It provided me the skills, knowledge, and tools to effectively respond to and handle APTs and other enterprise-wide threats.” Josh M., US Federal Agency |
FOR608: Enterprise-Class Incident Response & Threat Hunting: Enterprises today have thousands; maybe even hundreds of thousands - of systems ranging from desktops to servers, from on-site to the cloud. Although geographic location and network size have not deterred attackers in breaching their victims, these factors present unique challenges in how organizations can successfully detect and respond to security incidents. This course will help you identify and respond to incidents too large to focus on individual machines. This course will teach you:
|
FOR572: Advanced Network Forensics: Threat Hunting, Analysis, and Incident Response | GNFA: It is exceedingly rare to work any forensic investigation that doesn't have a network component. Endpoint forensics will always be a critical and foundational skill but overlooking their network communications is akin to ignoring security camera footage of a crime as it was committed. This course covers the tools, technology, and processes required to integrate network evidence sources into your investigations to provide better findings, and to get the job done faster. This course will teach you:
|
DFIR Job Role Matrix
To further help you navigate the best courses for your DFIR career, we have created a Job Role Matrix. This matrix provides you with a guide to match the most common job roles in DFIR with the courses that best fit the different skills to learn. Click on the image to download the file
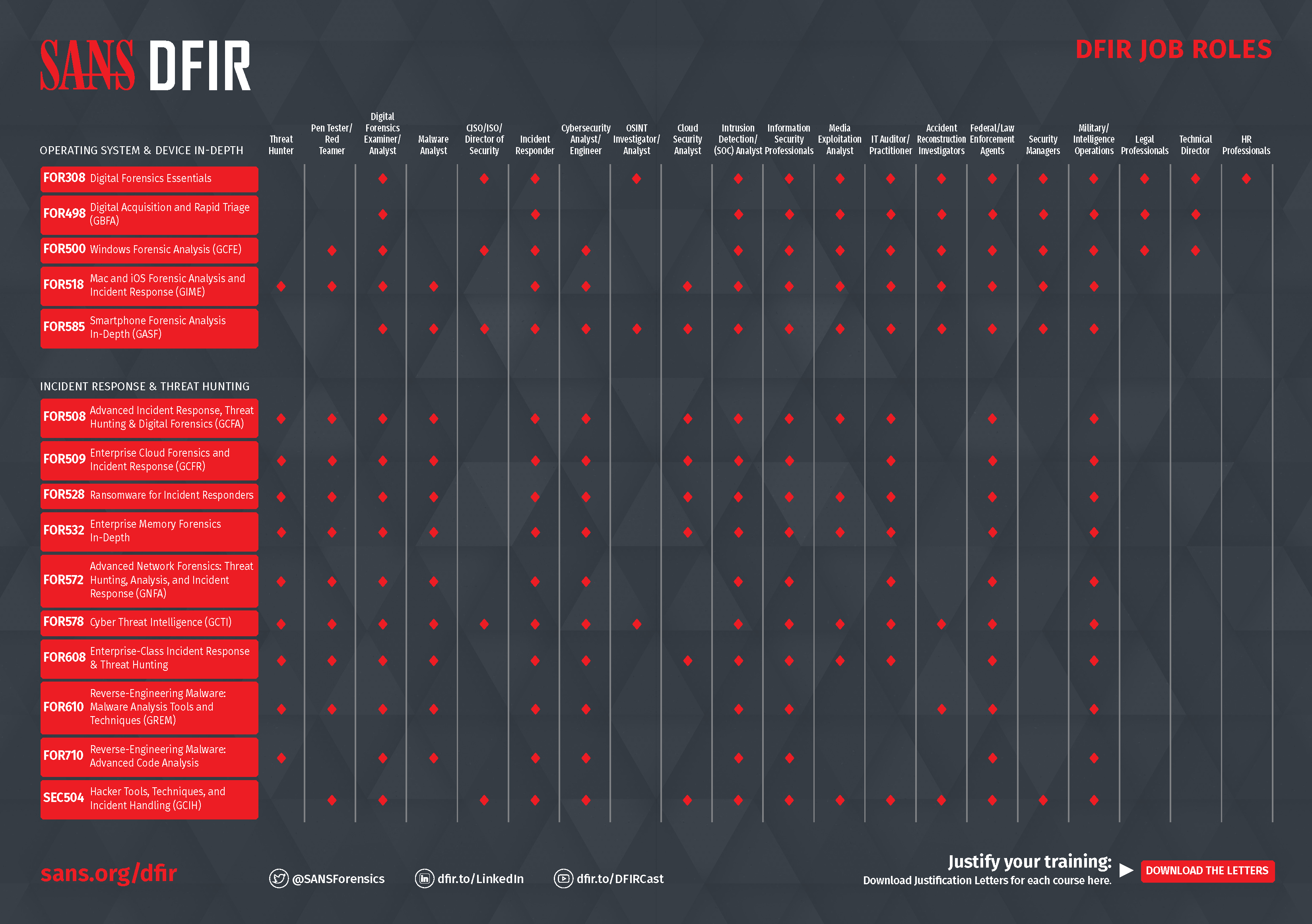
For more information about the SANS DFIR Courses visit: https://www.sans.org/u/1kD4

Need to justify your training? We have created justification letter templates for all the DFIR courses! Use these justification letters to share the key details of these courses and the certifications associated with each. Download them here
Viviana has over 15 years in the Digital Forensics and Incident Response (DFIR) industry and started her career as a Director of Marketing at some of the top digital forensic hardware acquisition and evidence analysis companies.
Read more about Viviana Ross