SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
Contact Us
Python 2 - The end of the world as we know it.
It will happen. In the year 2020 an event will occur that will alter the course of information security forever. What is this apocalyptic event? The end of life for Python 2. Is it that big of a deal? Meh. I'm just being dramatic. As of 2020 they will stop releasing updates and patches to Python 2. But Python 2 isn't going anywhere. If history has taught us lessons about what happens to unsupported software then we will continue to see it running critical infrastructure and hospital equipment for many years to come. Those programs that run in Python 2 interpreters today will continue to run in Python 2 interpreters well after 2020. Sadly today some organizations are still running old Python 2.5 interpreters despite the fact that it is now 13 years old and has serious security issues. It's pretty safe to say that we will continue to see Python 2 for the foreseeable future.
That said, I think it is a little short sighted to continue to develop new tools and automation in Python 2 today. Today you should definitely be developing new code that works in Python 3. Any new tools you purchase and plan to use for more than a year should run in Python 3. You should also evaluate the risk associated with running that old Python 2 interpreter that may have security vulnerabilities once it is no longer supported vs updating your code to work with a supported interpreter. As you look to the future you should do that with Python 3 in your sights.
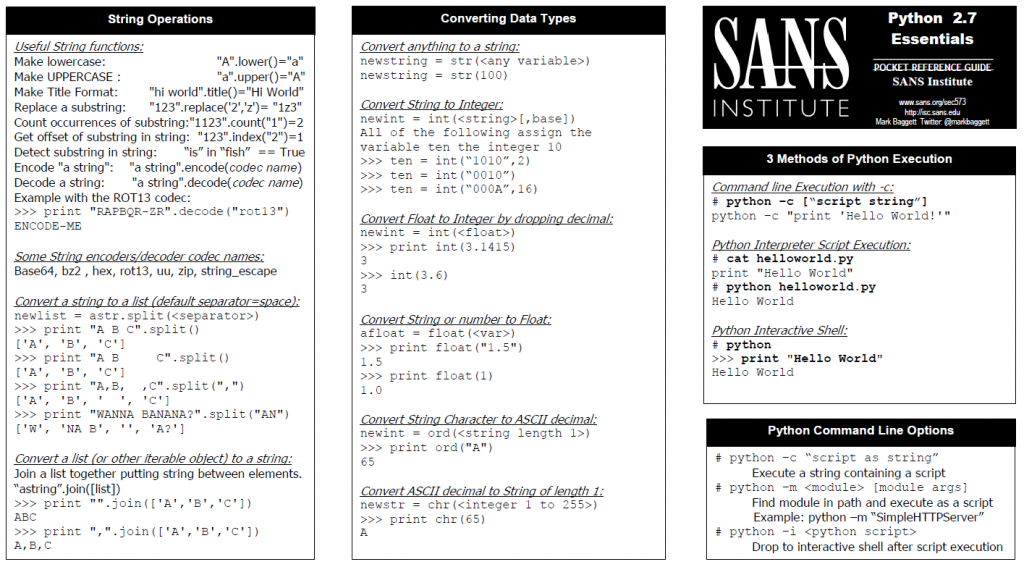
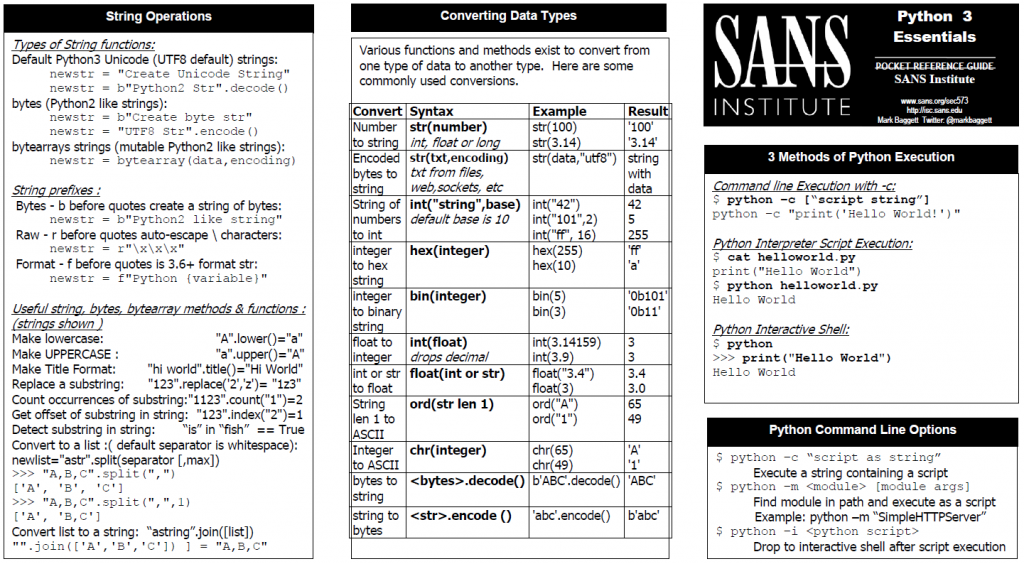
SANS SEC573: Automating information Security with Python course and the associated GPYC certification rides the Python2/Python3 fence along with the rest of the Industry. The course teaches you to build new tools for automation of common defensive, forensics and offensive task in Python 3. Developing new tools in Python 3 will set you up for success moving forward. We also covers what you need to know to convert your existing Python 2 code to Python 3. If you need to continue to use Python 2 we will teach you how to write code that is forward compatible to Python 3 so you are ready to switch when you are eventually forced to. In my opinion it isn't really a choice between Python 2 and Python 3. The answer is both. We will supporting both versions for a while. In celebration of that fact here are the SEC573 Python2 and Python3 cheat sheets available for you to download and print! Enjoy!
DOWNLOAD - Python 2.7 Cheat Sheet
DOWNLOAD - Python 3 Cheat Sheet


Mark Baggett has revolutionized cybersecurity through his leadership at SANS. His development of tools like Freq Server has strengthened threat detection, while his work in automation has empowered professionals to defend against evolving threats.
Read more about Mark Baggett