SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
Contact UsWhat?! There Are Critical Security Controls We Should Follow?

This is Part 2 of a 4-Part series. Read the other parts here.
In the Fall of 2020, SANS wrote a 3-part blog post about how to build a security program in a post breach scenario in a fictional organization called Rekt Casino. You can read those posts starting here. This blog post is based on the REKT Casino Hack Assessment: Operational webcast series, which you can view starting here.
To summarize what happened: Rekt Casino suffered a ransomware attack that resulted in a breach. The Ransomware came in over email due to no spam filtering, phishing or malware protections on the email server.
The initial malware was able to beacon out to the attackers because there were no outbound firewall rules. Memory dumps showed the attackers were using PSEXEC, PowerShell and an unknown executable. RDP connection were observed taking place on the network using the domain admin account – domain admin had been compromised.
Things were going really wrong at Rekt Casino. This post is about how the breach could have prevented by utilizing the tools and techniques available to cybersecurity professionals today in the form of the cyber hygiene principles developed through collaboration between the SANS Institute, the Center for Internet Security, and thousands of other cybersecurity professionals from around the world.
The sad fact about this scenario, and so many other examples of cybersecurity breaches, is that they could have been prevented. Yes, hackers are intelligent and are diligently looking for the mistakes that an organization might make. But that does not mean that organizations like Rekt had no idea what they needed to do in order to defend themselves. Cyber attackers are not magicians. They cannot wave a magic wand and simply break into an organization. They can only take advantage of weaknesses or a lack of solid defenses in order to abuse an organization’s information systems.
Dozens of cybersecurity control libraries or standards have been created over the years to address this challenge. Governments, industry groups, and volunteer organizations have all worked together over the years to define the controls an organization must put into effect in order to prevent breaches like this from occurring. Just a few of the more popular of such standards include the following:
And this is just the tip of the iceberg. Every year new groups release research defining the controls that could be used to effectively stop a cyber-attack.
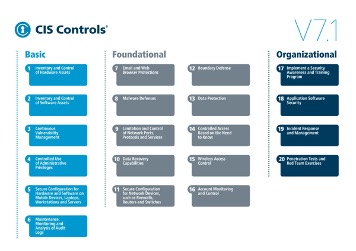
One of the more popular documents to define a standard of cybersecurity care is the Center for Internet Security (CIS) Controls (formerly known as the Critical Security Controls and Consensus Audit Guidelines). This document was originally published as a collaboration between the SANS Institute and the US National Security Agency, along with dozens of other contributors from other US federal agencies and the private sector. The goal of this project was to define a specific set of prioritized, technical controls, that organizations could implement that would effectively prevent the attacks that face organizations every day.
In the course of developing the CIS Controls, there were a number of guiding principles that were also developed to guide the project and give direction to the writing and implementation of each of the controls. The core guiding principles are:
One of the best things about these controls is that they were not created in a vacuum. Instead, they are the result of numerous entities working together to provide feedback into the attacks that they are seeing and the controls that they’ve found, which are helpful in truly combating these threats. The individuals that contributed to the project have experience in fighting the threats directly and have given insight from their experiences.
More specific information about this project can be found at https://www.cisecurity.org/.
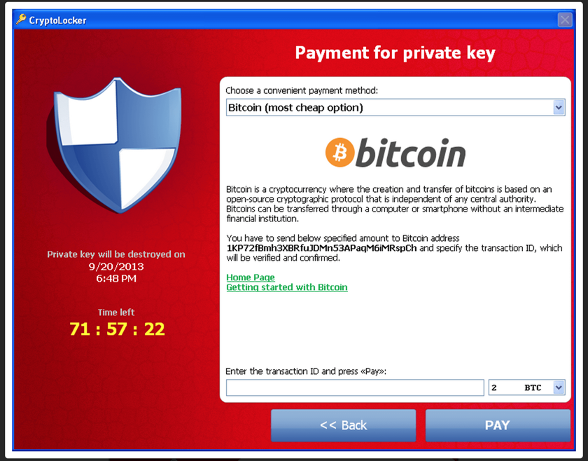
In this specific incident, the attackers who broke into Rekt Casino decided to use ransomware as a major piece of their toolkit. Ransomware attacks, especially targeted ones, are becoming more and more common as cybercrime groups look to monetize their hacking activities. Law enforcement groups have found that cybercrime groups are even beginning to specialize in specific aspects of an overall breach. One group may collect access to organizations after they successfully establish a foothold in the organization. Another group may be focused on monetizing that access through theft of intellectual property, ransomware, or other similar activities.
There are a number of defensive controls with the capability to defend against ransomware attacks like the one observed here. Specifically, some of the most relevant control families with the ability to block this attack are as follows:
It is a combination of these controls that provides an organization with the greatest chance at preventing an attack, detecting if an attack is being attempted, or recovering from the attack if it is successful. The more mature an organization is, and the further in their journey they are implementing these control families, the more likely they will be able to stop any attack targeted against them.
In short, the people at Rekt Casino had access to the knowledge that could have prevented this incident. No one in cybersecurity wants to blame the victims of attacks such as this and doing so would never be fair. But the other side of this coin is that the cybersecurity industry knows what needs to happen if an organization wants to defend itself against this type of attack. Step-by-step, prioritized guidance exists. That does not mean that it will be easy or free to do what is necessary. But if organizations like Rekt use the resources available to them and methodically implement the controls prescribed, they can be successful at stopping such directed attacks.
Any organization considering this approach should:
Effective cybersecurity will not always be easy or free, but it is possible and achievable by all.
James Tarala is a principal consultant with Enclave Security based out of Venice, Florida, and a SANS Senior Instructor. As a consultant, he has spent the past several years designing large enterprise security and infrastructure architectures, helping organizations to perform security assessments, and communicating enterprise risk to senior leadership teams. He is the co-author and an instructor for SEC566: Implementing and Auditing the Critical Security Controls and MGT415: A Practical Introduction to Cyber Security Risk Management. Learn more about James.


James Tarala, managing partner at Cyverity, co-created the CIS Controls and Cybersecurity Standards Scorecard, transforming cybersecurity governance and empowering global organizations to operationalize risk into actionable defense strategies.
Read more about James Tarala