SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
Contact Us

NMAP is an ideal choice for port scanning, but sometimes it may not be a feasible option. Other times a quick check to see if a port is open might be all the detail needed. In these scenarios PowerShell really shines. Let's examine methods to use PowerShell for basic port scanning functionality.

PowerShell port scanner:
1..1024 | % {echo ((new-object Net.Sockets.TcpClient).Connect("10.0.0.100",$_)) "Port $_ is open!"} 2>$nullTest-Netconnection scan a range of IPs for a single port:
foreach ($ip in 1..20) {Test-NetConnection -Port 80 -InformationLevel "Detailed" 192.168.1.$ip}PS IP range & port range scanner:
1..20 | % { $a = $_; 1..1024 | % {echo ((new-object Net.Sockets.TcpClient).Connect("10.0.0.$a",$_)) "Port $_ is open!"} 2>$null}PS test egress filtering:
1..1024 | % {echo ((new-object Net.Sockets.TcpClient).Connect("allports.exposed",$_)) "Port $_ is open!" } 2>$nullTo create a PowerShell port scanner in one line we need to combine three distinct components. Creating a range of objects, looping through each object, and outputting information for each to the screen. In the case of PowerShell we can make use of its object oriented nature to facilitate this process.
PowerShell port scanner:
1..1024 | % {echo ((new-object Net.Sockets.TcpClient).Connect("10.0.0.100",$_)) "Port $_ is open!"} 2>$null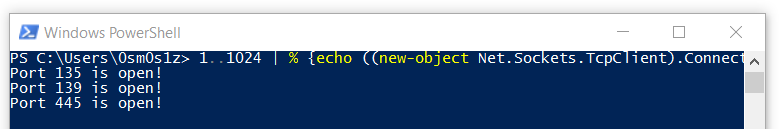
1..1024 | % {echo ((new-object Net.Sockets.TcpClient).Connect("10.0.0.100",$_)) "Port $_ is open!"} 2>$null
<pre>1. 1..1024 - Creates a range of variables between 1..1024</pre>2. | - The pipe operator passes objects into the loop3. % - The % operator in PowerShell is an alias for foreach-object, and is used to start a loop.
The loop executes the content between {} in sequence4. echo - Print the following output to the screen5. new-object Net.Sockets.TcpClient - Instantiates an instance of the .Net TcpClient class, allowing us to make socket connections to TCP ports6. .Connect("10.0.0.100",$_)) - Call the Connect function on the TcpClient class with arguments 10.0.0.100 and port $_. $_ is a variable that means current object.
The current object relates to number (1..1024) that the loop is currently on.7. "Port $_ is open!") - This prints Port # is open! when the program finds an open port.8. 2>$null - This tells PowerShell not to display any errors encounteredThe range above scans the 1024 low number ports, but it can easily be adjusted ie (22..53), (8000..9000), etc.
Another method available from within PowerShell is the "Test-NetConnection" command which can dump extended useful information and is very similar:
foreach ($ip in 1..20) {Test-NetConnection -Port 80 -InformationLevel "Detailed" 192.168.1.$ip}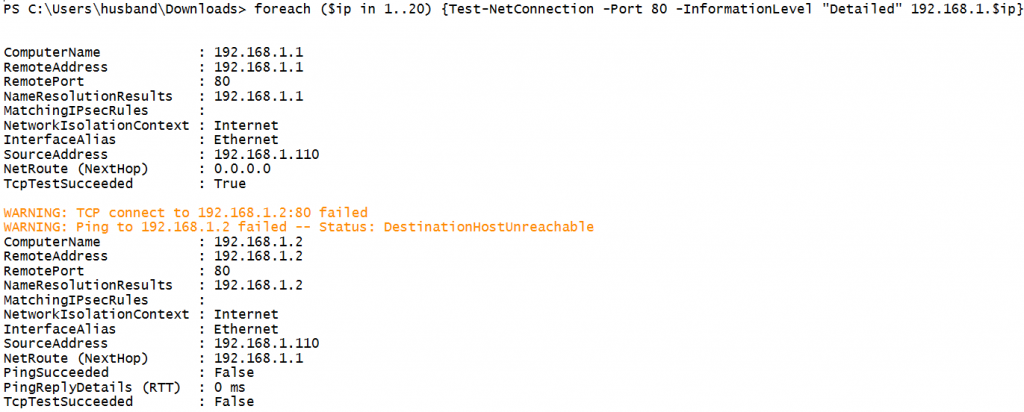
A major downside to the Test-NetConnection option is that it was not introduced until PowerShell version 4.0.
foreach ($ip in 1..20) {Test-NetConnection -Port 80 -InformationLevel "Detailed" 192.168.1.$ip}
1. foreach ($ip in 1..20) {} - Loop through numbers 1 to 202. Test-NetConnection - Test-NetConnection is a utility for testing different types of network connectivity.3. -Port 80 - Check the availability of port 804. -InformationLevel "Detailed" - Provide detailed output information5. 192.168.1.$ip - Attempt to connect to port 80 against the listed IP address.
The $ip variable loops from 1-20 in this example.Building a scanner that iterates through systems and ports is possible as well:
PS IP range & port range scanner:
1..20 | % { $a = $_; 1..1024 | % {echo ((new-object Net.Sockets.TcpClient).Connect("10.0.0.$a",$_)) "Port $_ is open!"} 2>$null}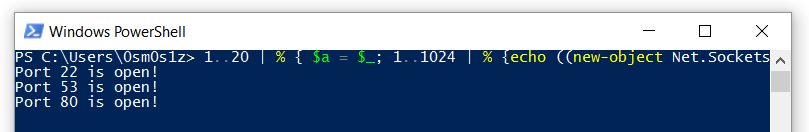
This version of the command will scan IP addresses 10.0.0.1-20 and ports 1-1024. Be advised, it may take a while to complete. A more efficient alternative might be to specify the ports to look for manually. Like this:
PS IP range & port range scanner v2:
1..20 | % { $a = $_; write-host "------"; write-host "10.0.0.$a"; 22,53,80,445 | % {echo ((new-object Net.Sockets.TcpClient).Connect("10.0.0.$a",$_)) "Port $_ is open!"} 2>$null}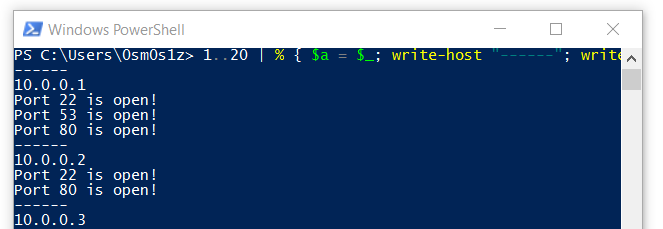
Many secure environments enable egress filtering controls to limit outbound protocol access to necessary services. This is one of the reasons it is advantageous to leverage HTTP/HTTPS/DNS channels where possible however, when in need of identifying alternative outbound access we can use PowerShell internally to evaluate egress filters on the network firewall.
PS test egress filtering:
1..1024 | % {echo ((new-object Net.Sockets.TcpClient).Connect("allports.exposed",$_)) "Port $_ is open" } 2>$null
For more information on PowerShell egress testing Beau Bullock with Black Hills Information Security has a detailed write-up here: http://www.blackhillsinfosec.com/?p=4811
PowerShell is a robust tool that can accomplish nearly anything when unleash on a Windows environment. Tinker with new and unique combinations of the commands discussed here and feel free to include your improvements in the comments below.
Matthew Toussain https://twitter.com/0sm0s1z


Launched in 1989 as a cooperative for information security thought leadership, it is SANS’ ongoing mission to empower cyber security professionals with the practical skills and knowledge they need to make our world a safer place.
Read more about SANS Institute