SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
Contact UsIn this article we look at a handy function to simplify Base64 encoding and decoding of data in PowerShell.

As PowerShell power user James Honeycutt points out, PowerShell supports Base64 encoding and decoding of data:
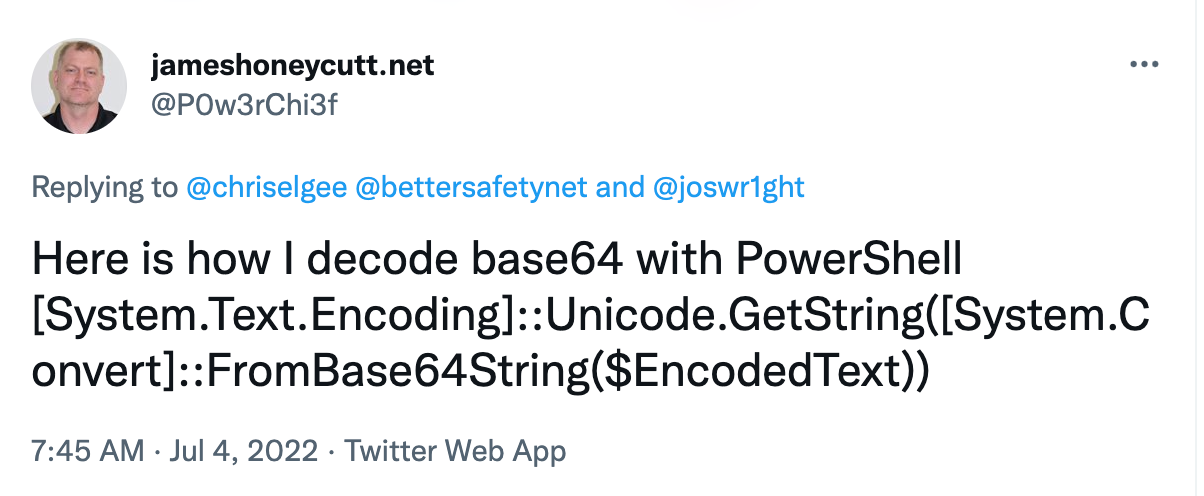
Here it is in text form:
[System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String($EncodedText))Let's break down this command piece-by-piece:
If you need to decode Base64 content often (for example, you work in threat intel, or malware analysis, or incident response), this is not terribly convenient to type. This is a good candidate to be summarized with a simple PowerShell function that you load in your default PowerShell profile.
A PowerShell profile is a script that runs automatically when you launch PowerShell. It allows you to customize your environment to suit your needs, but it requires that you permit PowerShell script execution policy on your system (which is disabled by default, for silly reasons; you can change the policy to allow local script execution, but not allow scripts downloaded from the internet by running [code]Set-ExecutionPolicy RemoteSigned -Force[/code] in an administrative PowerShell session).
To create a handy function to simply Base64 decoding, open your PowerShell profile in Notepad or your favorite editor using the [code]$profile[/code] variable:
PS C:\Users\Sec504> notepad $profile
PS C:\Users\Sec504>Next, paste in the following functions to add [code]ConvertFrom-Base64[/code] and [code]ConvertTo-Base64[/code] as PowerShell commands:
Function ConvertFrom-Base64($base64) {
return [System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String($base64))
}
Function ConvertTo-Base64($plain) {
return [Convert]::ToBase64String([Text.Encoding]::ASCII.GetBytes($plain))
}Next, reload your PowerShell profile using the [code]&[/code] call operator (or, close and open a new PowerShell session):
PS C:\Users\Sec504> & $profile
PS C:\Users\Sec504>PS C:\Users\Sec504> ConvertTo-Base64("Hello Base64")
SGVsbG8gQmFzZTY0
PS C:\Users\Sec504> ConvertFrom-Base64("SGVsbG8gQmFzZTY0")
Hello Base64
PS C:\Users\Sec504>In these simple functions, I am converting the data to ASCII strings, which is normally what I want. If you are working with data that needs another form of conversion (such as decompressing data), then I'll probably just copy-paste [code][System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String($EncodedText))[/code] from my Obsidian notebook.
-Joshua Wright
Return to Getting Started With PowerShell
p.s. My #monthofpowershell collaborator Mick Douglas is wrapping up his article on customizing your PowerShell profile in amazing ways. Stay tuned for that to publish soon!
Joshua Wright is the author of SANS SEC504: Hacker Tools, Techniques, and Incident Handling, a faculty fellow for the SANS Institute, and a senior technical director at Counter Hack.


As Senior Technical Director at Counter Hack and SANS Faculty Fellow, Joshua has advanced cybersecurity through ethical penetration testing, uncovering critical vulnerabilities across Fortune 500 companies and national infrastructure providers.
Read more about Joshua Wright