SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
Contact UsUnderstanding the ss command is crucial for analyzing network connections & traffic, to identify and investigate potentially malicious activities.

The ss (socket statistics) command is a powerful tool in Linux used for examining sockets. As an incident responder, understanding the ss command is crucial for analyzing network connections and traffic, particularly in identifying and investigating potentially malicious activities. Unlike the older netstat command, ss is faster and displays more detailed information, making it invaluable in modern incident response scenarios.
The basic usage of ss is straightforward. When executed without any options, ss lists all open sockets. To refine this, various options can be applied. For example, ss -t displays TCP sockets, ss -u shows UDP sockets, ss -l lists listening sockets, and ss -a shows both listening and non-listening sockets.
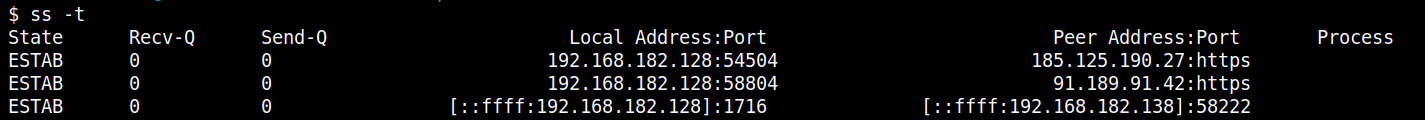
Filtering is a key feature in ss. Incident responders can use ss to filter sockets based on states like established, listen, syn-sent, syn-recv, fin-wait-1, etc. For instance, ss state established will list all established connections.
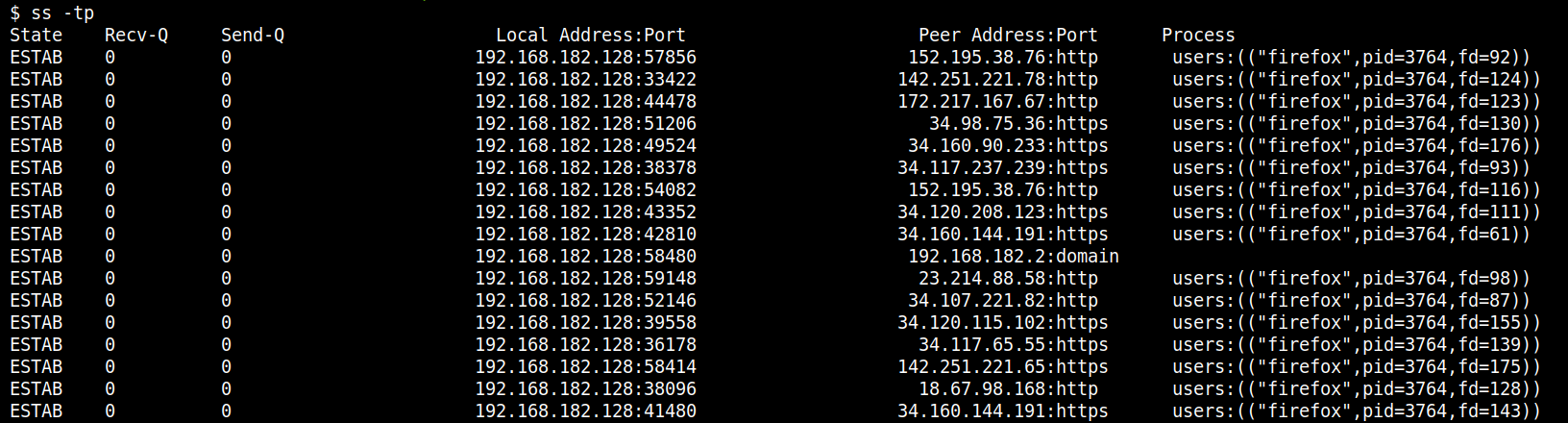
One of the most powerful features of ss is its ability to display process information linked to sockets. Using ss -tp, you can view the process ID (PID) and process name associated with each socket. This is particularly useful for tracing back network activity to specific processes.
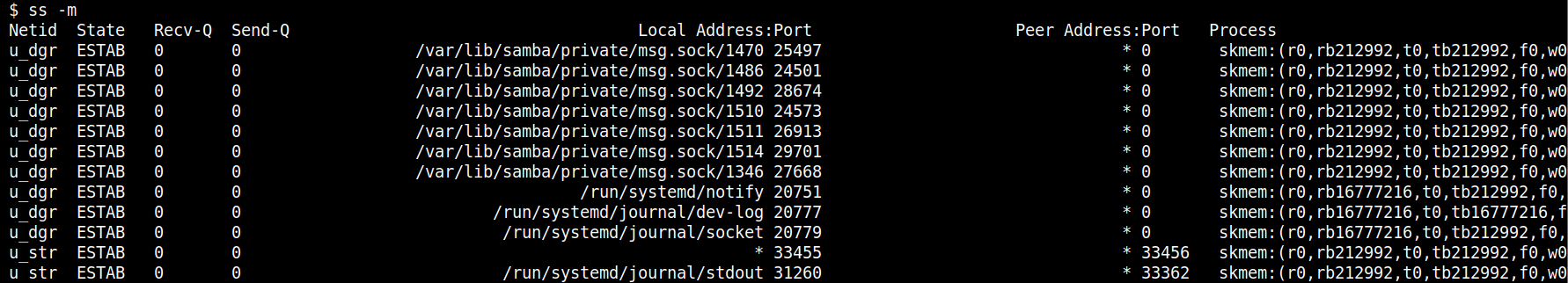
For more detailed analysis, ss -ie displays extended information like TCP congestion control algorithm used and ss -m shows socket memory usage statistics. These extended details can be crucial in diagnosing performance issues or detecting unusual patterns indicative of malicious activities.
Incident responders often need to identify outbound connections that could be indicative of exfiltration or C2 (Command and Control) activities. Using ss, one can filter for established connections on unusual ports or to unfamiliar IP addresses. For example, ss -tp state established dport = :[PORT_NUMBER] lists all established TCP connections on a specific port and shows the process involved.

Monitoring for unexpected listening ports is another critical activity. ss -tuln lists all TCP and UDP ports on which the system is listening, helping to identify unauthorized services or backdoors.
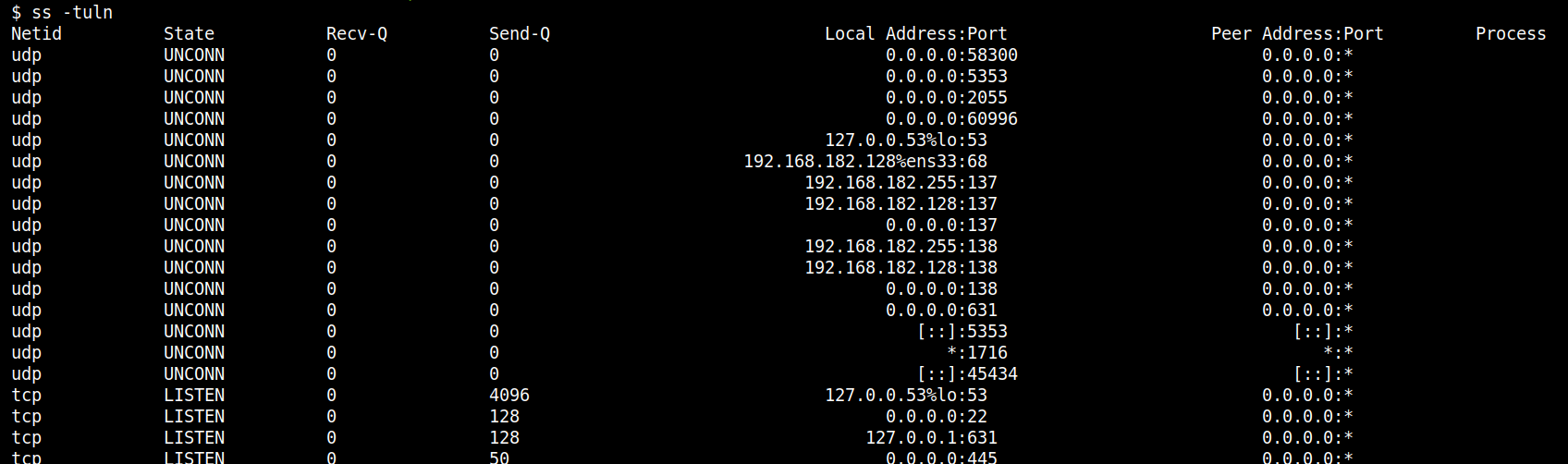
In the context of C2 or data exfiltration, unusual traffic patterns are a red flag. Commands like ss -tan state established can be used to view all (listening and non-listening) TCP connections, which can then be further analyzed for suspicious activity.
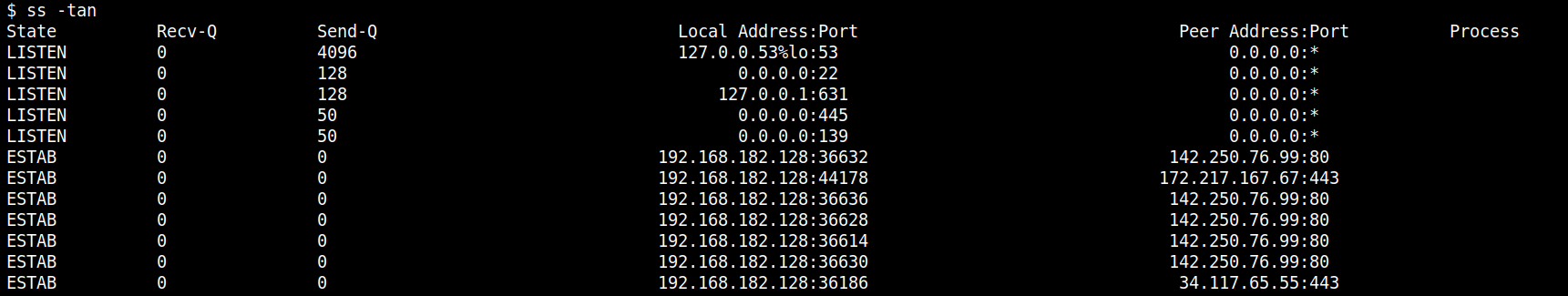
When a suspicious connection is identified, using ss -tp to find the PID and process name can lead to the source of the malicious activity. This can be critical in understanding the scope and impact of a security incident.
If you are normally a netstat user, you can easily move over to using ss on Linux platforms. For example, the typical netstat command used for DFIR is netstat -anop. This means: show all sockets (listening and non-listening), show numerical addresses, show timer information and show process ID.
You can replicate this with ss by using
ss -ntaup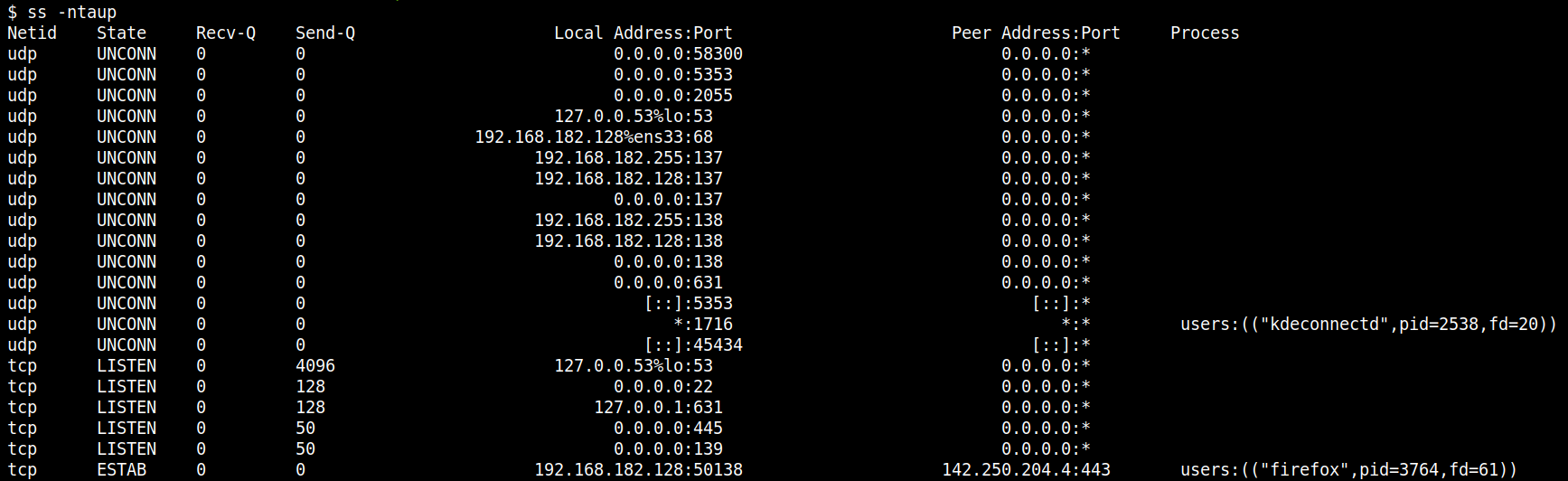
The ss command is a versatile and powerful tool for incident responders. Its ability to provide detailed socket information, coupled with advanced filtering and process association capabilities, makes it essential for modern network traffic analysis and incident investigation. By mastering ss, incident responders can efficiently identify, analyze, and respond to various network-related security incidents, especially in the realms of unauthorized access, C2 communications, and data exfiltration attempts.
If you would like to know more about this, and Linux Incident Response in general, have a look at the SANS Institute course FOR577 Linux Incident Response and Threat Hunting. You can find out more about this course at https://sans.org/for577


With FOR577, Taz has authored the first course to systematize threat hunting on Linux systems. His operational leadership—from military intelligence to heading a FTSE100 CSIRT—has fortified global cyber defense capabilities across sectors.
Read more about Tarot (Taz) Wake