SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
Contact UsFor forensic analysts working in Windows environments, .lnk shortcut files and the thumbprint caches are valuable sources for details about missing data.
Individuals wanting to hide their activities may flush their browser cache, Temp files, use, and even wipe the drive free space. However, they may forget these two minor "tidbits". These can show detail, indicate actions and associated history. Be Warned, I have found Windows machines having thousands of .lnk files on a "scrubbed PC."
The shortcut (.lnk) file is an amazing mine of information for such a small file. This PDF (See Link) is an invaluable source describing the details of the shortcut .lnk. The shortcut file name format is usually name.ext.lnk There may be multiple .lnk files created for one file depending upon the type.
XP stores the .lnk files for the Word 2007 Document Brains.docx in:
%Drive%:\Documents and Settings\User ID\RecentThe above .lnk (..\Recent)is slightly larger
%Drive%:\Documents and Settings\User ID\Application Data\Microsoft\Office\RecentWindows 7 stores these .lnk files in
%Drive%:\Users\sdd\AppData\Roaming\Microsoft\Windows\RecentThe above .lnk (..\Recent) is twice the size of the second.
%Drive%:\Users\sdd\AppData\Roaming\Microsoft\Office\Recent.lnk File properties show only a tip of available information. Compare the same Word 2007 Brains.docx.lnk file for XP and Windows 7. I use XVI32 as my hex-editor for details about the type of storage, location, Volume Serial number and much more.
Review the XP Hex dump example below. Then, compare the two different hex dumps of Windows 7 .lnk files. (You may need to zoom to inspect the images.) I did not include all of the first .lnk file hex.
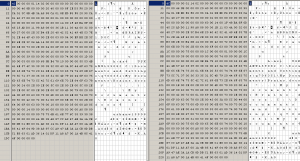
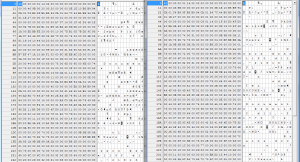
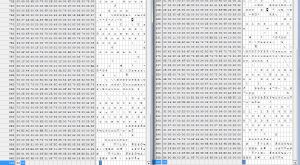
Thumbs or Thumbnails are also invaluable source of data. I will discuss them in my next posting. I will then tie the Thumbnails and Shortcuts together.
XVI32 Hex Editor: http://www.chmaas.handshake.de/delphi/freeware/xvi32/xvi32.htm
Steven is the senior member of an IT Security team for a Bio-Pharma company. He has presented to a variety audiences including SANS, Midwest Consolidated Security Forum and various local chapters of HTCIA and ISACA. His current focus is Certificate Management, Encryption and Incident Response. With a science degree unrelated to IT, Steven has over 20 years in Information Technology with the past 13 years in Security. He has earned among the various vendor certificates, his CISSP (#3700), CISA (#153869) as well as GIAC G7799 (#151) Silver and GCFA (#18) gold certifications.
Whether you're seeking to maintain a trail of evidence on host or network systems or hunting for threats using similar techniques, larger organizations are in need of specialized professionals who can move beyond first-response incident handling to analyze an attack and develop an appropriate remediation and recovery plan.
Read more about SANS DFIR