SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
Contact UsHopefully at one point in time everyone has experienced the enjoyment of a teacher that allowed them to use a "cheat sheet" on a test. For the unfamiliar, the concept is simple; take an 8.5 x 11" piece of paper, cram as much information as you can on both sides, and use it as an open reference for a test. The key was not only to put as much information as you could fit on the two-sided document, but for that information to be neatly organized and readily accessible so you could quickly reference information and articulate answers before the test clock ran out.
Without hesitation, it can be challenging to memorize commands and too consuming at other times to search through #DFIR resources (online resources, books, notes, contacts, and etc) to answer questions like "Is there an alternative to mounting split .e01 image in SIFT workstation if mount_ewf.py fails?" or "How do I create a GREP statement that shows me all sources in a timeline?"
It was not long until I found myself taking the "cheating" outside of school and into my #DFIR career. Within months I found it instrumental to create cheat sheets for all types of tools and processes including imaging using dc3dd, GREP expression examples, exporting mailboxes using Microsoft Exchange cmdlets, and etc. At first I thought it was a great personal resource, but then everyone who saw them wanted a copy! I found that beginners used them as guides and experts liked them to reference the command they rarely used.
As a novice user of "off the shelf" forensic products, I naturally gravitated to the SANS SIFT workstation when I heard about its capabilities (and NO cost!). It was great to see an open source initiative in the #DFIR community, such as log2timeline, that had features in some respect that would only be expected from expensive off the shelf products.
After reading Rob Lee's blog titled, "How to Make a Difference in the Digital Forensics and Incident Response Community" I thought to myself, perhaps if I created a cheat sheet for log2timeline it would make a difference? You be the judge. At the #SANS360 event in DC I released what will hopefully be one of many cheat sheets to come.
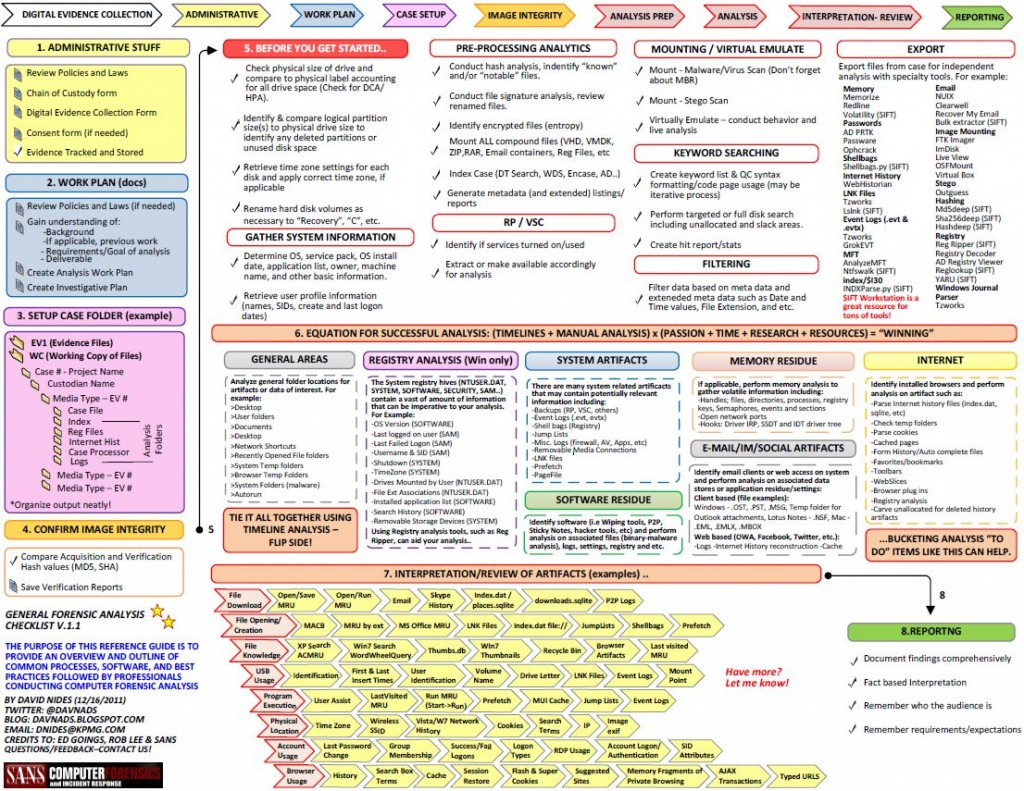
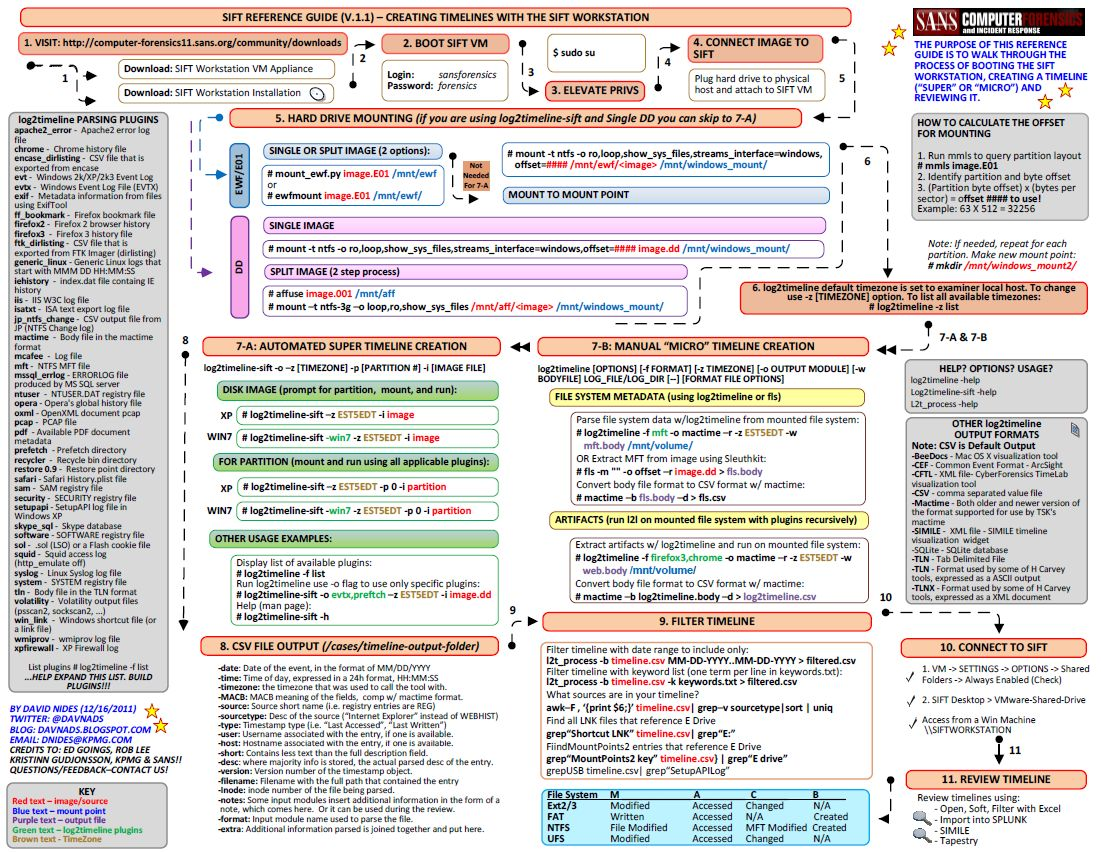
Note: It's intended to be printed in color, double-sided and laminated. Credits to Ed Goings, Rob Lee, Kristinn Gudjonsson, and SANS for content.
About author:
David Nides is a Senior in KPMG's Forensic Technology Services practice in Chicago, IL. He currently plays a lead role in KPMG's national Incident Response team consulting clients globally in APT, data breach, and other cyber crime investigations. You can follow David on twitter @davnads or at his forensic blog.