SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
Contact UsSEC541 is a threat-driven class for the cloud. Learn how to build a detection engineering program for your organization.

SEC541: Cloud Security Attacker Techniques, Monitoring, and Threat Detection now spans across 5 comprehensive sections. The course remains focused on providing in-depth case studies of cloud attacks, equipping learners with the ability to employ cloud services for investigating suspicious activities within their cloud infrastructure, and imparting the necessary skills to security analysts and detection engineers for creating a top-tier detection and response program. With this expansion, students can expect an even more extensive and immersive learning experience that will prepare them to tackle complex cloud security challenges with confidence.
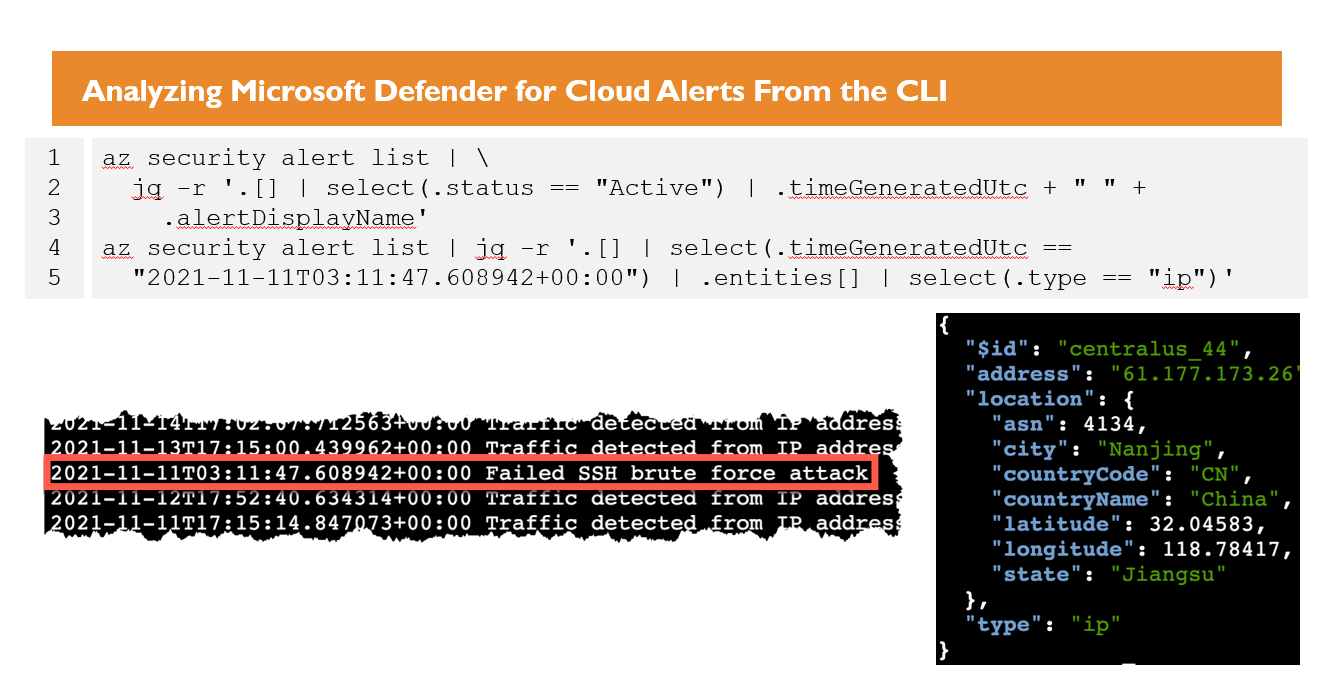
As part of the expanded 5-section course, we have introduced a dedicated section that delves into the unique aspects of the Azure environment. Here, you will learn how to investigate data collected from Microsoft 365 Exchange and Azure Active Directory using cutting-edge techniques. You will also become proficient in using the Azure CLI, as well as leveraging powerful tools like Microsoft Defender for Cloud and Sentinel. Additionally, you will learn about the Kusto Query Language, which is a powerful tool for analyzing large datasets in Azure. To further enhance your skills, you will also gain hands-on experience building automated response actions to accelerate investigations and strengthen your security posture. By the end of this section, you will be well-equipped to handle any security challenge with confidence.
SEC541 starts each section with a case study walkthrough of an attack campaign against a cloud infrastructure. We break down how it happened, what made it successful, and what could have been done to catch the attackers in the act.
"I enjoyed understanding the real life use cases for each of the topics and how it linked with a known attack (Capital One)." - Shakiya Linley, JP Morgan Chase
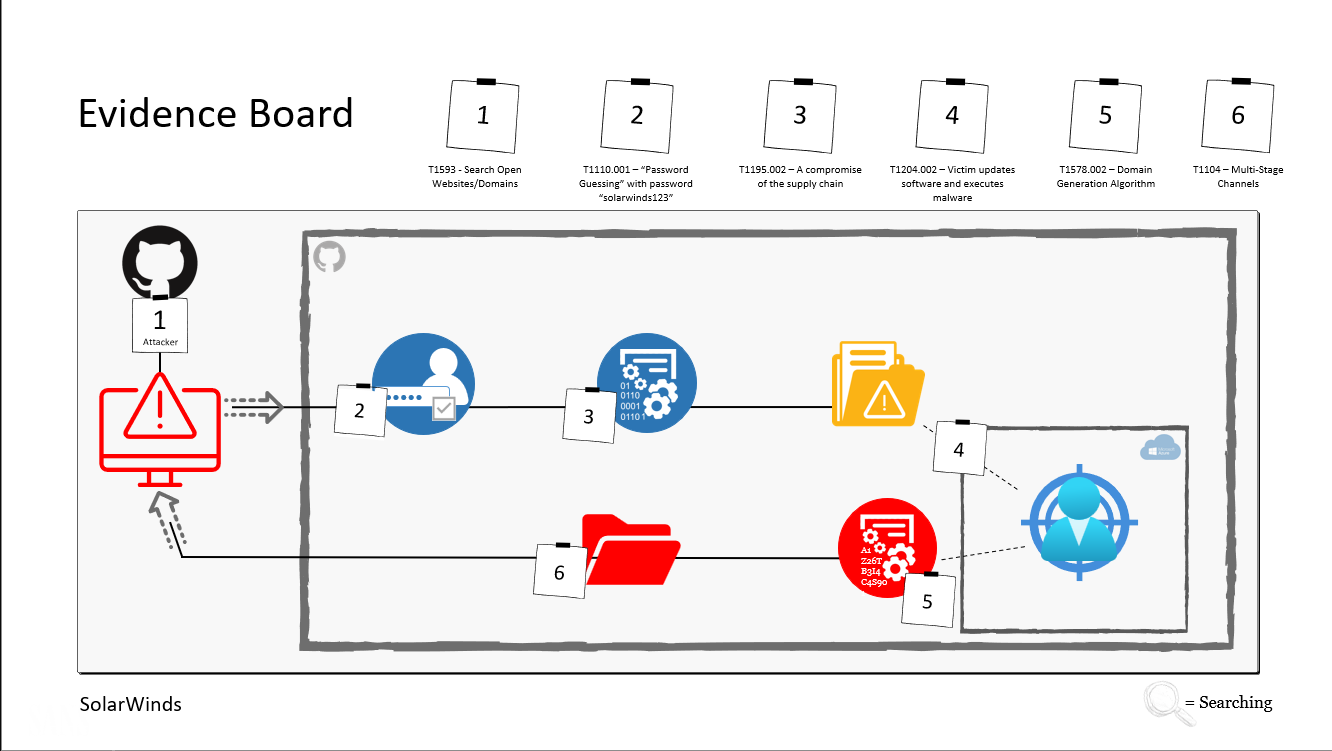
After dissecting the attacks, we learn how to leverage cloud-native and cloud-integrated capabilities to detect, threat hunt, or investigate similar attacks in a realistic environment, and build our arsenal of analytics, detections, and best practices. "Using the labs was easy with well documented instructions. I like the fact that I could easily copy and paste the commands. This helps me to get through the lab fast but I also know that I can come back later after the course and take the time to review each command." - Ludek Suk, Accenture
The class culminates with a CloudWars challenge: a capture-the-flag style event where individuals or teams are faced with challenges from throughout the week.

The winning team will get to take home theSEC541 challenge coin!



Shaun McCullough spent 20+ years at the NSA working in cyber operations as a software engineer and technical director of Blue, Red, and Hunt teams. He is currently a staff level Cloud Security Engineer at GitHub.
Read more about Shaun McCullough