SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
Contact UsThe SANS CloudSecNext was a free, global, virtual event for the community. Check out these graphic recordings created in real-time throughout the even
On June 3rd and 4th, thousands from around the globe tuned in for the SANS CloudSecNext Summit. Industry’s top practitioners and leading experts from around the globe shared actionable ideas, methods, and techniques for building and maintaining a secure cloud infrastructure with the community. It was a great opportunity for cybersecurity professionals and those new to the field.
We invited Ashton Rodenhiser of Mind's Eye Creative to create graphic recordings of our Summit presentations. If you missed a talk or are looking to view the SANS CloudSecNext Summit through a visual lens, take a look at the recordings below.
In addition to graphic recordings, PDFs of Summit presentations are available on the SANS Summit Archives page (SANS account required) and videos will be posted to YouTube over the next several months.
*If you registered for the Summit, video recordings will be available on your Summit Access page in your SANS Portal next week!
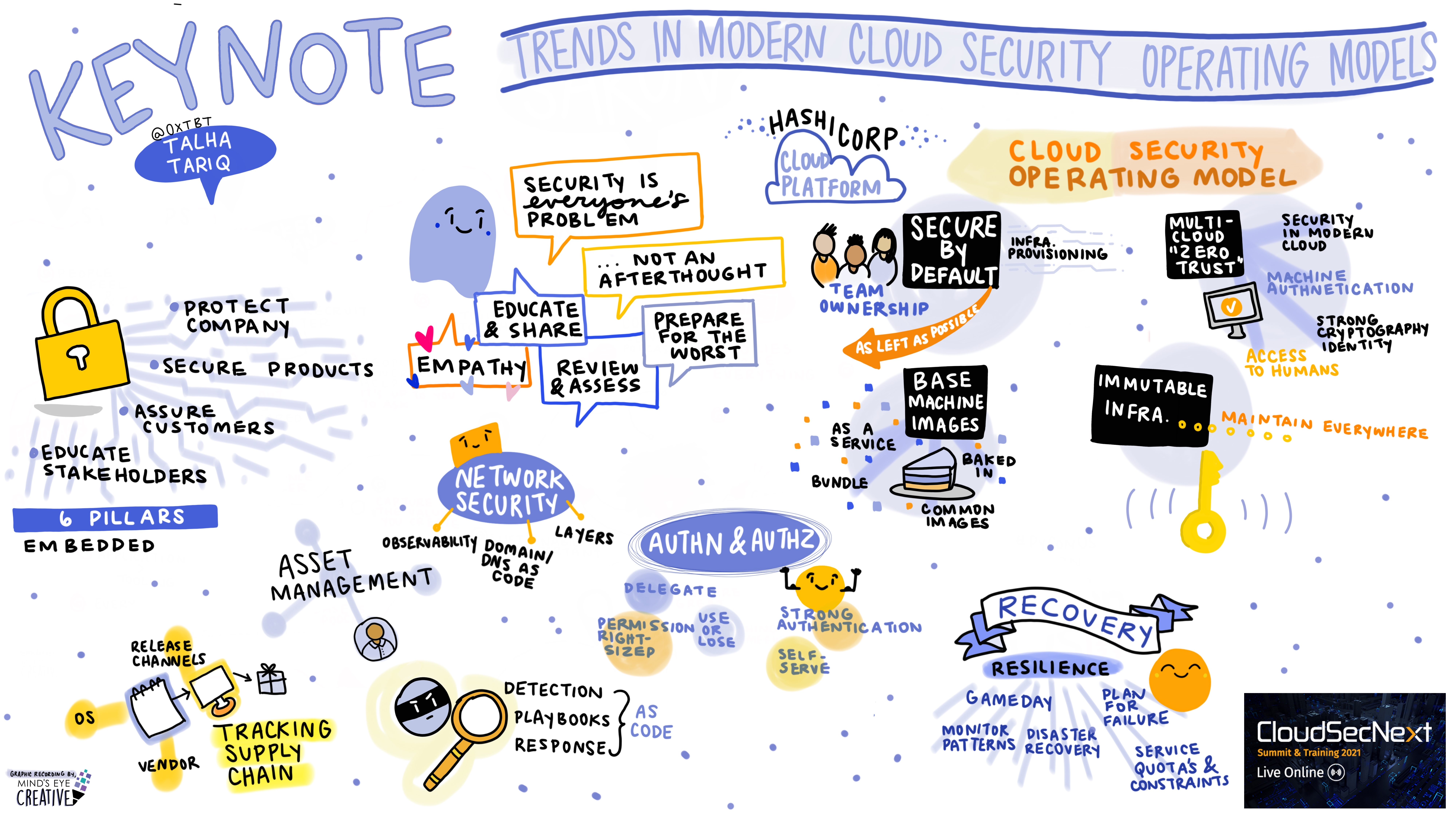
Keynote: Trends in Modern Cloud Security Operating Models Talha Tariq @0xtbt, Vice President & Chief Security Officer, HashiCorp
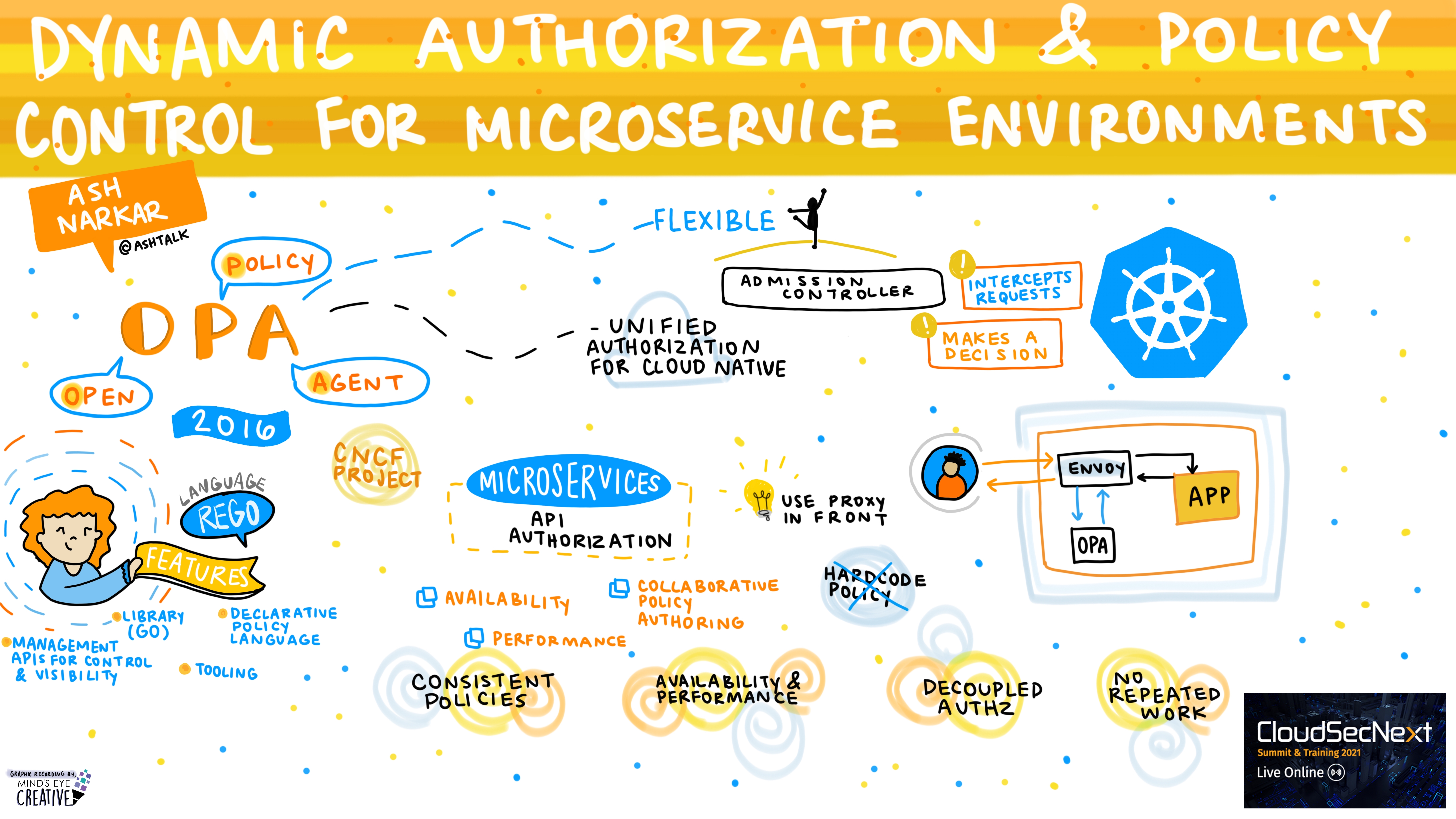
Dynamic Authorization and Policy Control for Microservice Environments Ash Narkar @ashtalk, Software Engineer at Styra | Maintainer – Open Policy Agent
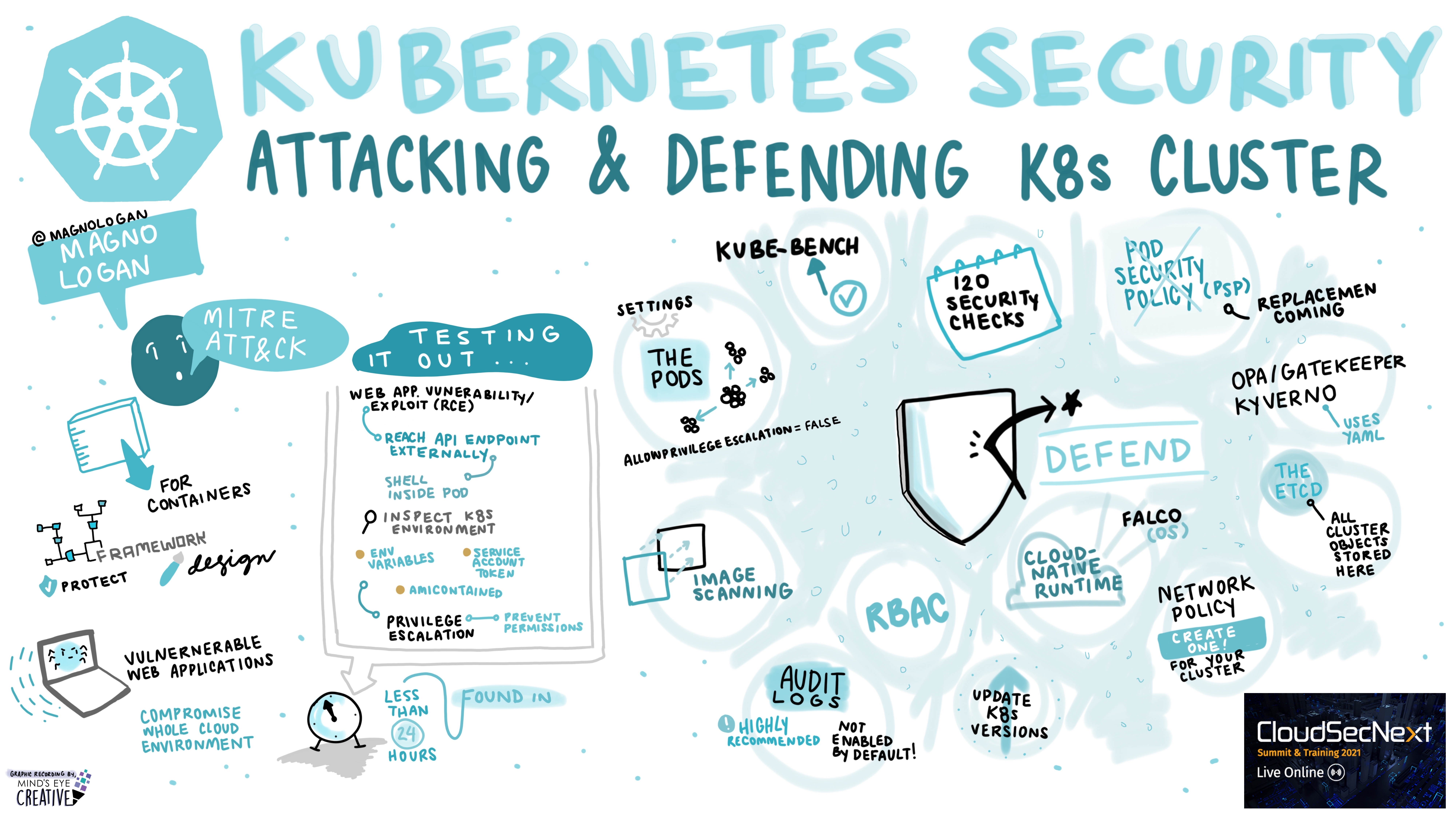
Kubernetes Security: Attacking and Defending K8s Clusters Magno Logan @magnologan, Information Security Specialist, Trend Micro
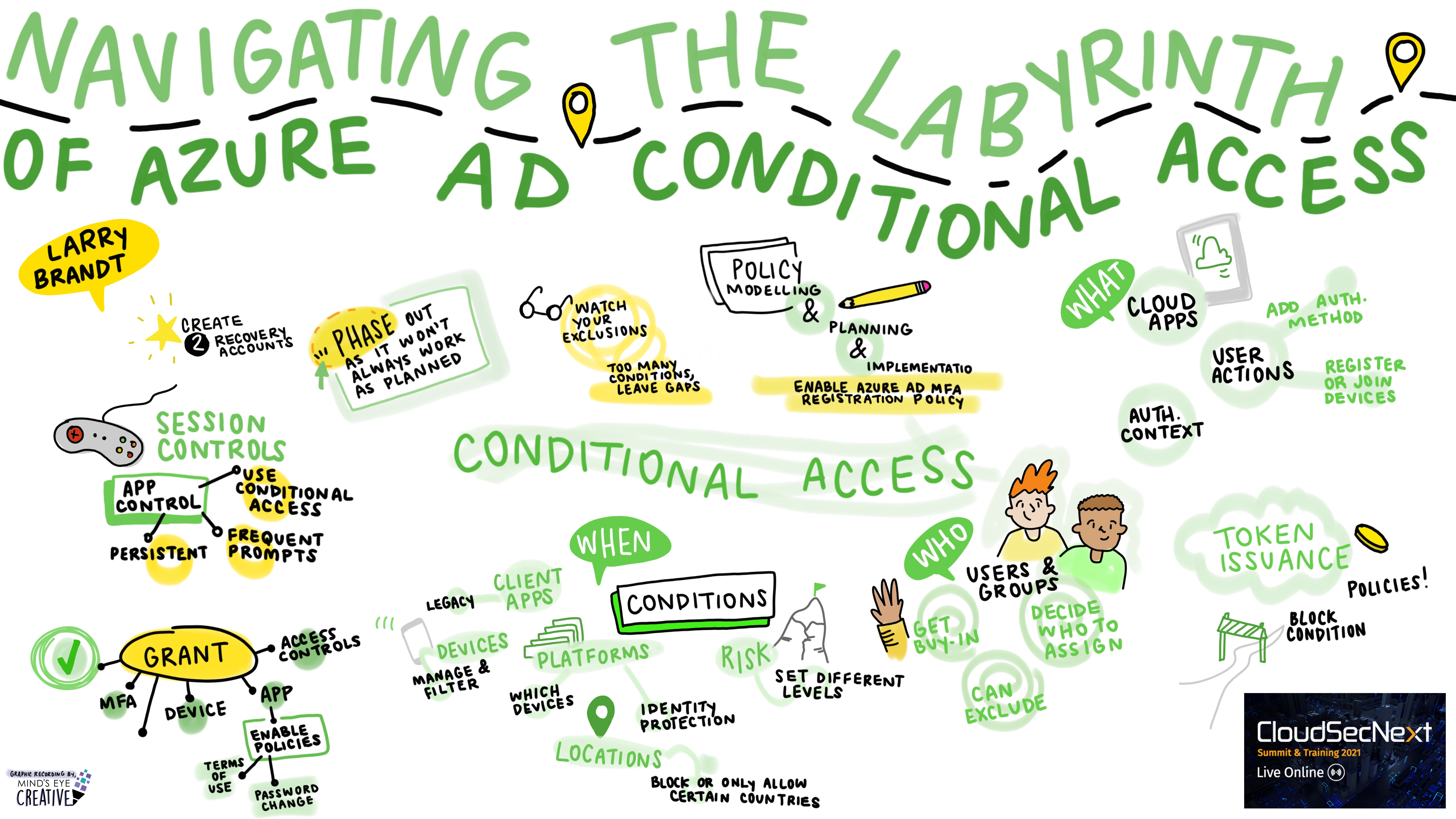
Navigating the Labyrinth of Azure AD Conditional Access Larry Brandt, Founder, Envision Cyber
Implementing an Effective Multi-Account Strategy on AWS AJ Yawn @AjYawn, Co-Founder and CEO, ByteChek
.jpg)
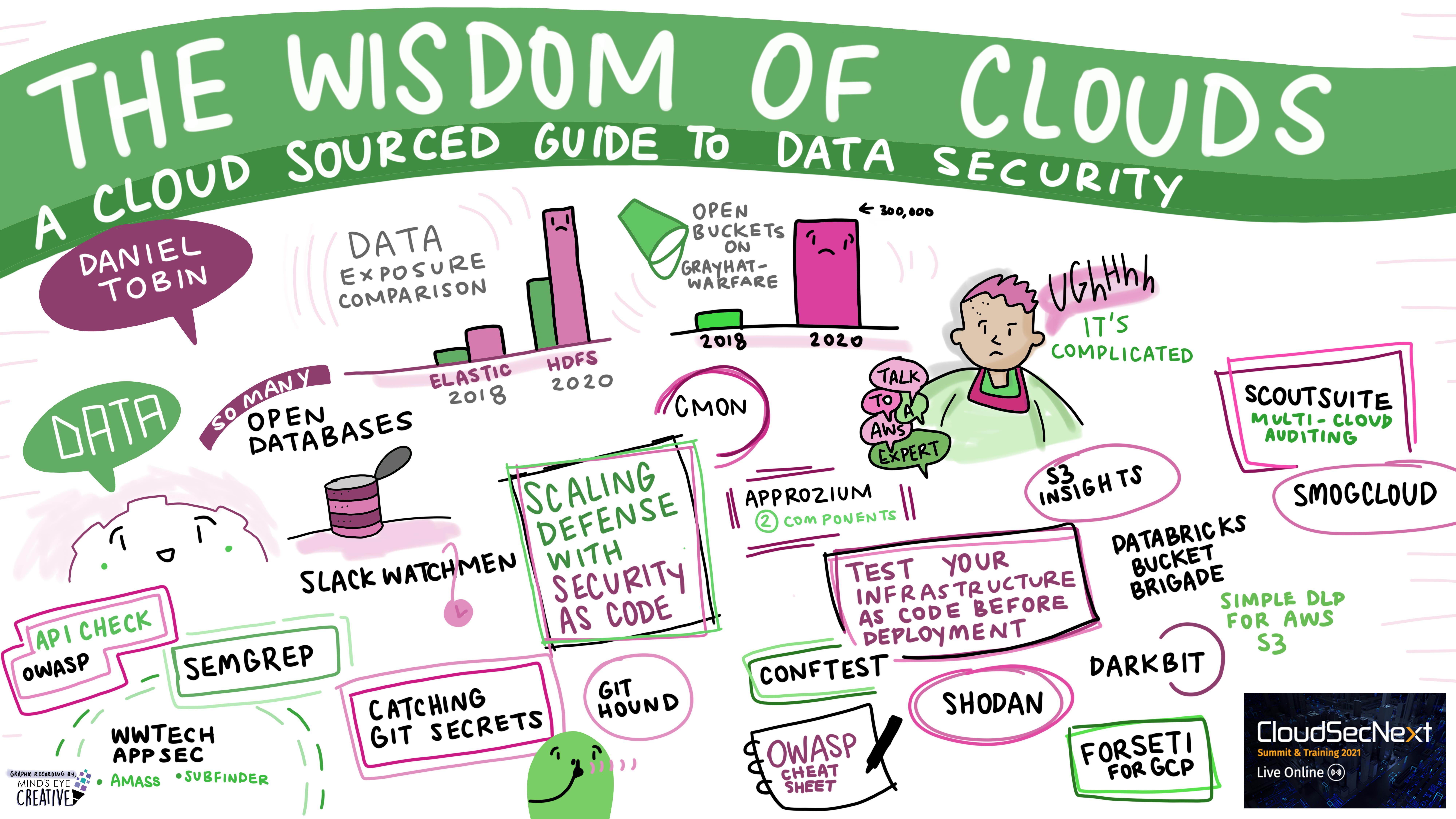
The Wisdom of Clouds: A Cloud Sourced Guide to Multicloud Data Security Daniel Tobin @dant24, Security Lead, Cyral Inc.
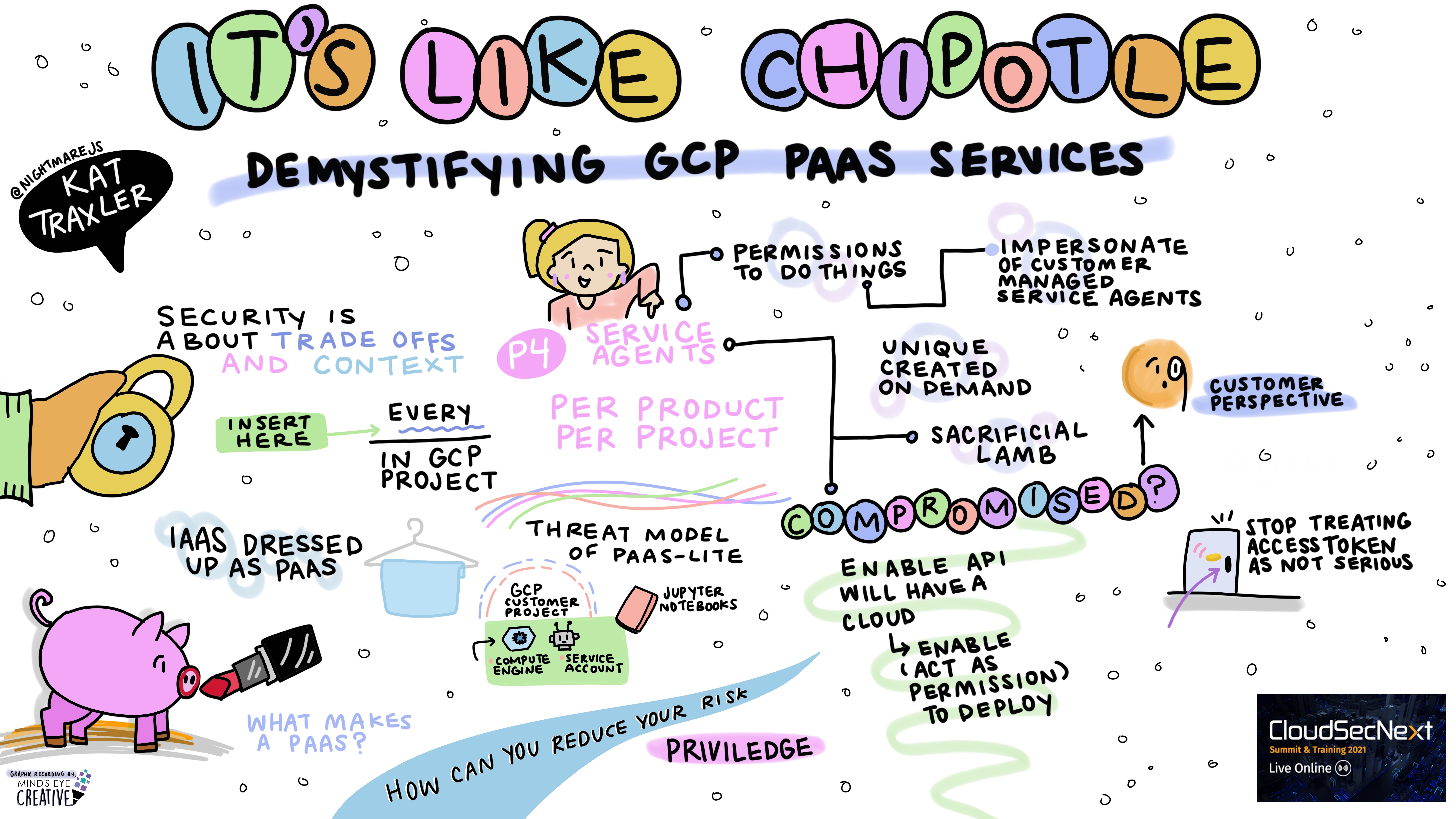
It’s Like Chipotle – Demystifying GCP PaaS Services Kat Traxler @NightmareJS, Cloud Security Engineering, Best Buy
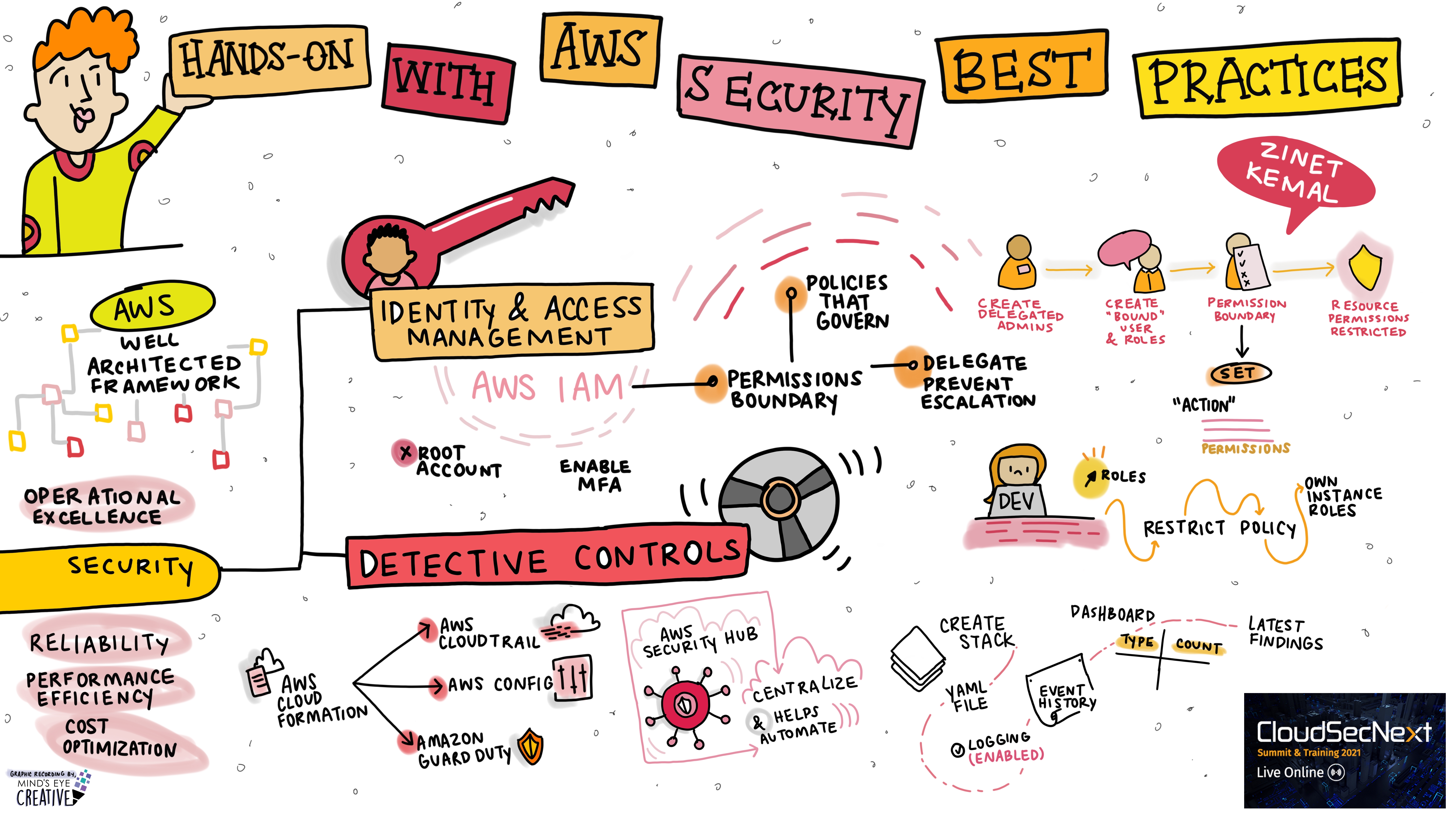
Hands-On with AWS Security Best Practices Zinet Kemal, Information Security Engineer, State of MN
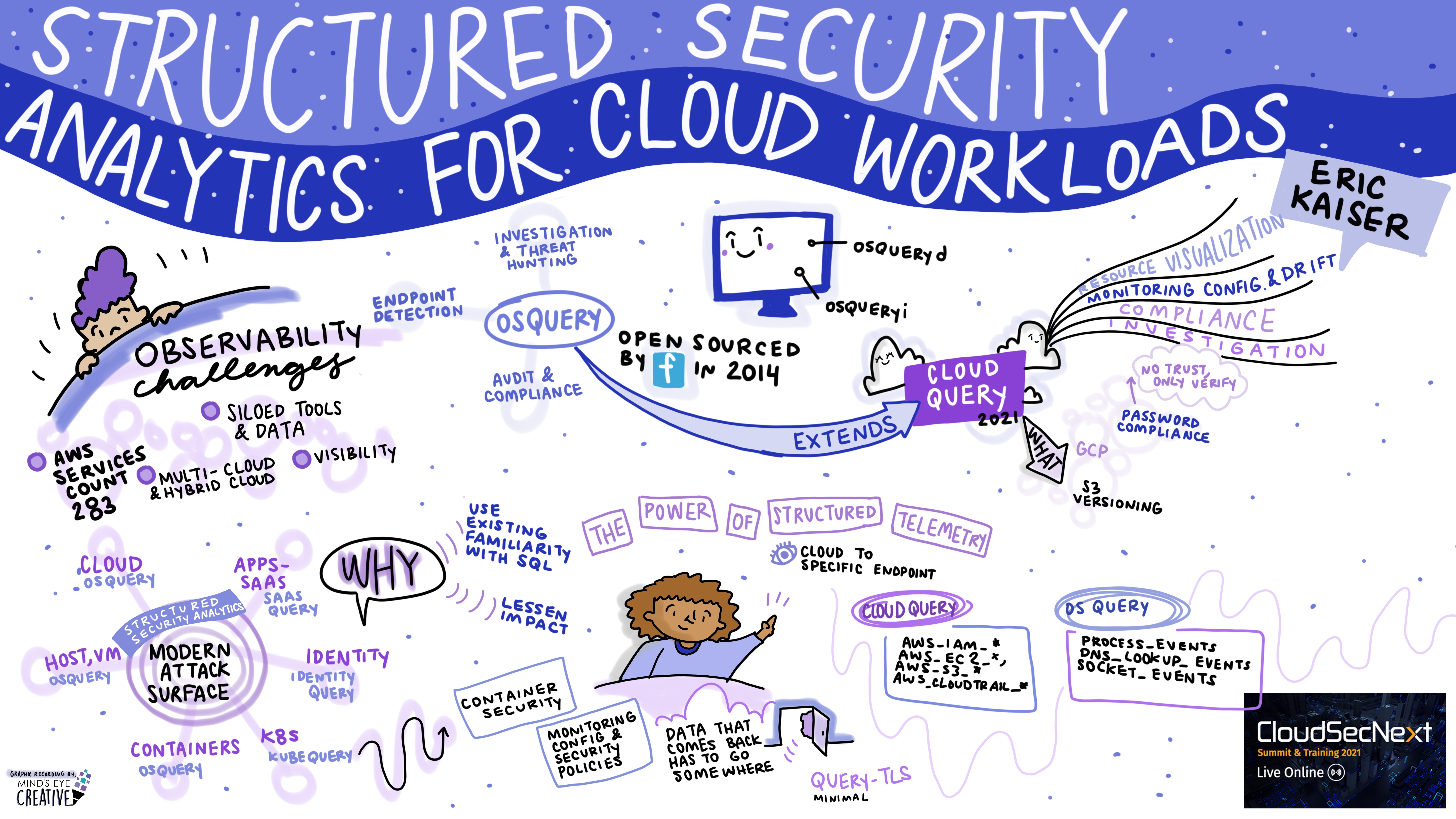
Structured Security Analytics for Cloud Workloads Eric Kaiser, Security Engineer, Uptycs
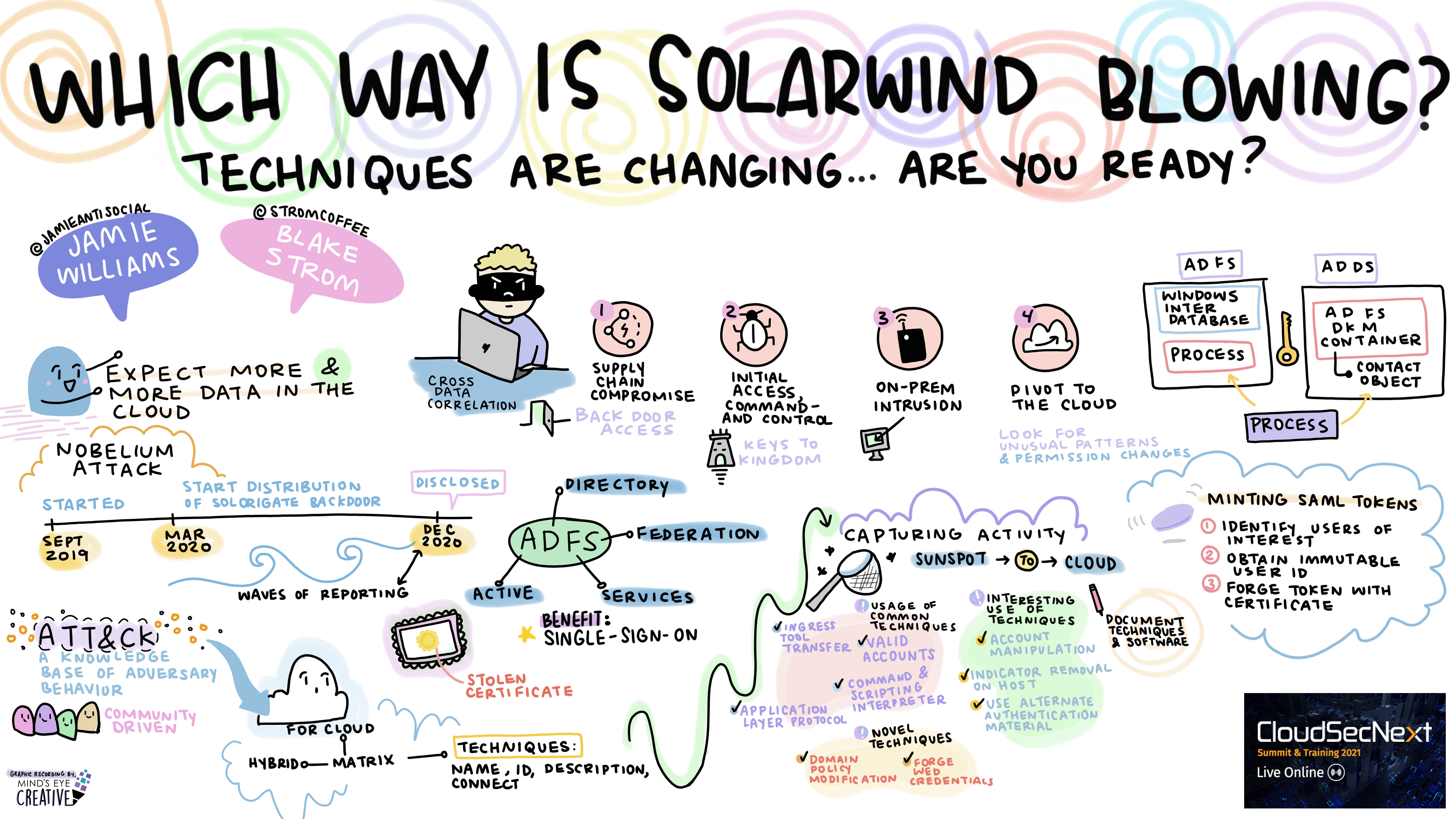
Keynote: Which Way is the SolarWind Blowing? Techniques Are Changing…Are You Ready? Jamie Williams @jamieantisocial, Lead Cyber Adversarial Engineer, The MITRE Corporation Blake Strom @stromcoffee, Principal Security Researcher, Microsoft
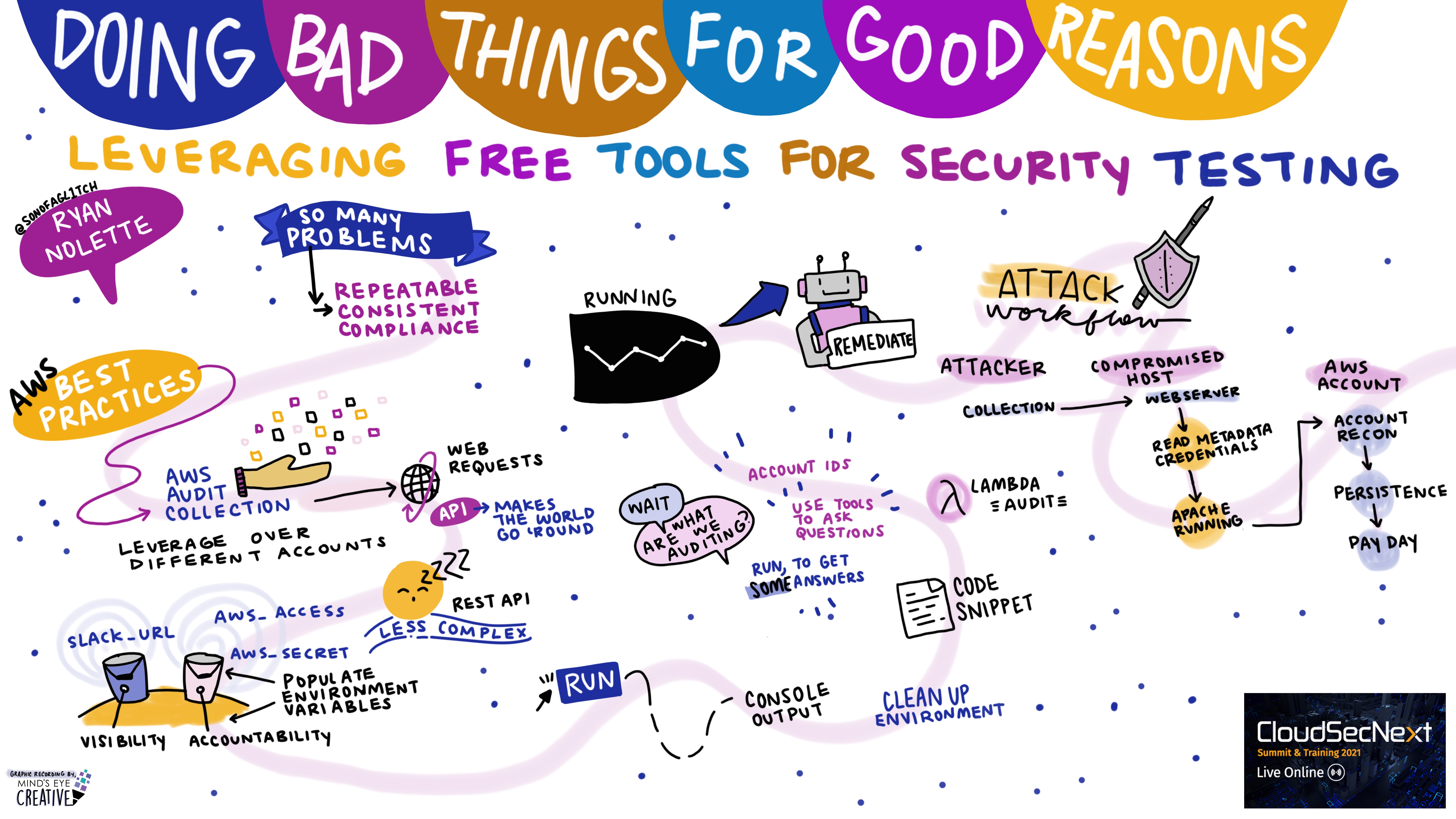
Doing Bad Things for Good Reasons: Leveraging Free Tools for Security Testing Ryan Nolette @sonofagl1tch, Security Technical Lead, Postman
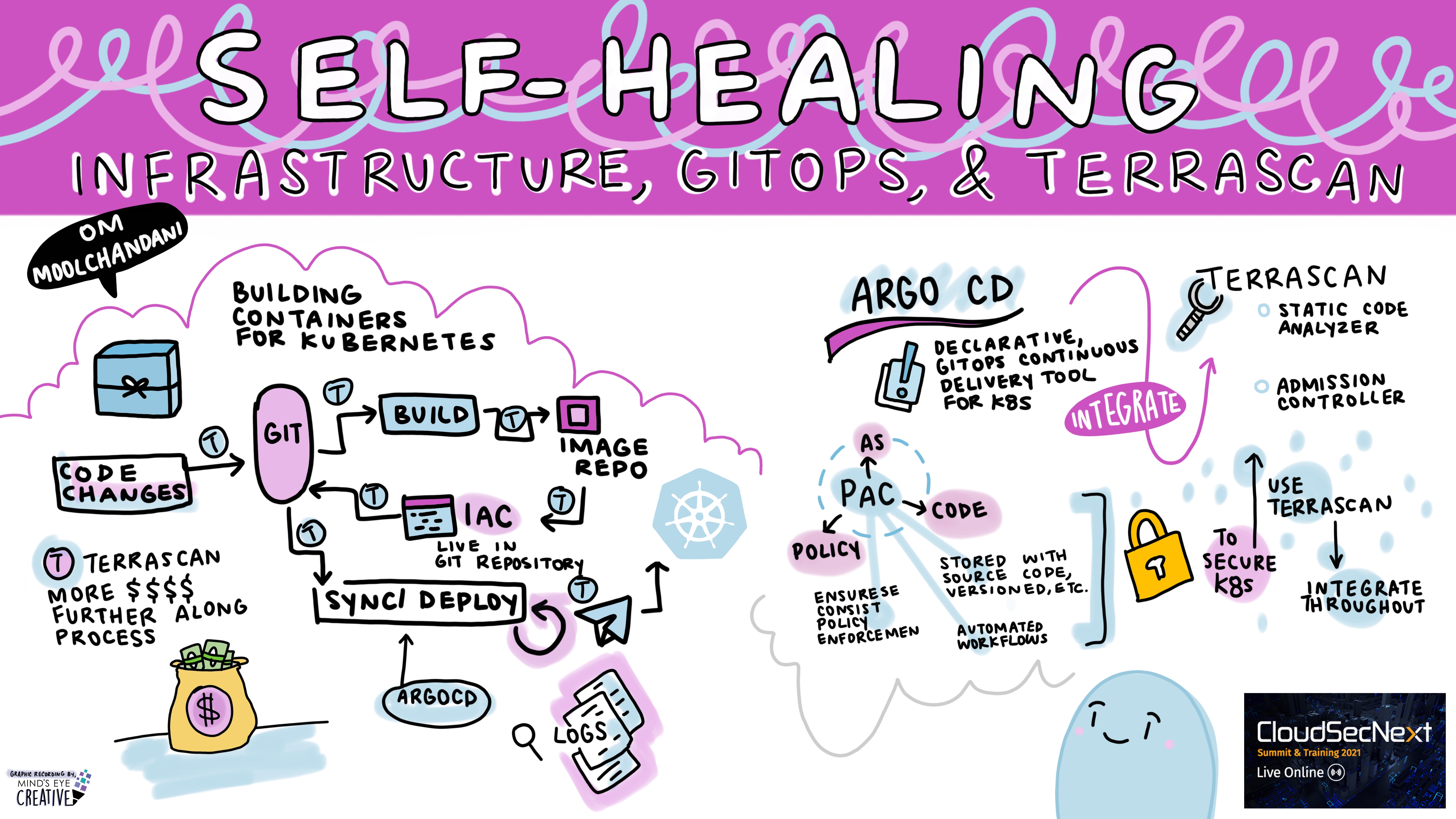
Self-Healing Infrastructure, GitOps, and Terrascan Om Moolchandani, CTO and Co-founder, Accurics
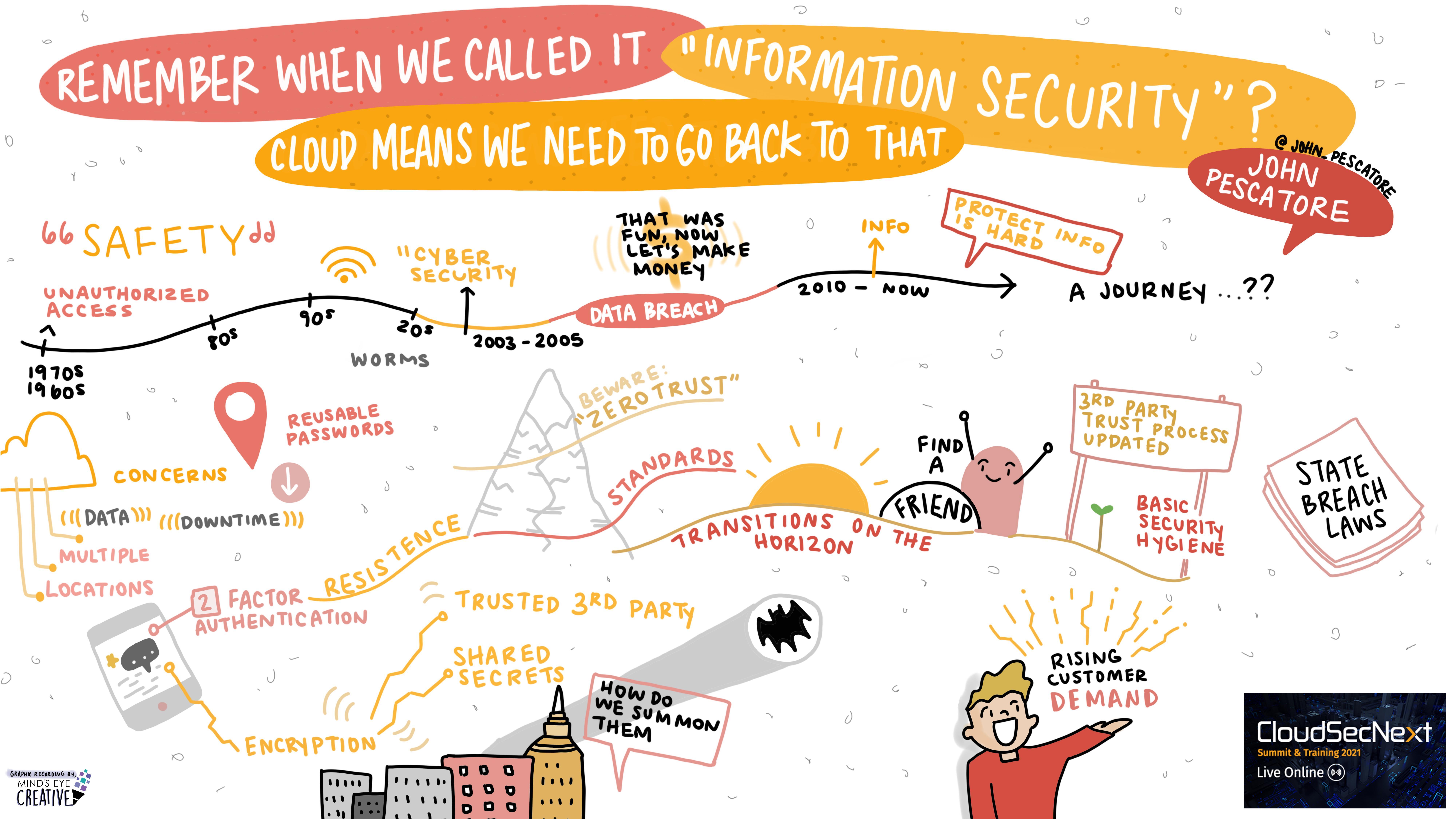
Remember When We Called It “Information Security?” Cloud Means We Need to Go Back to That John Pescatore @john_pescatore, Director of Emerging Security Trends, SANS Institute
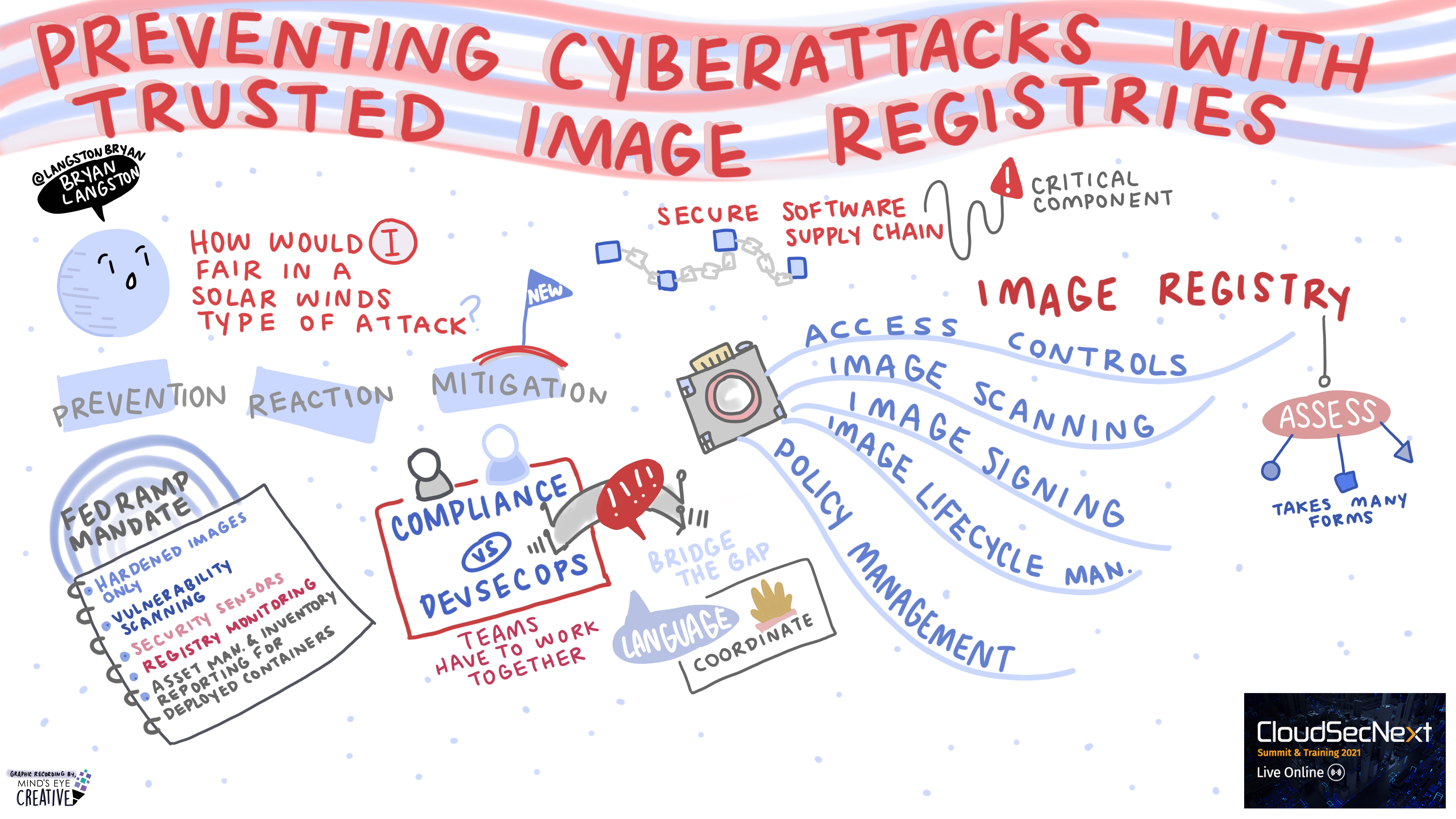
Preventing Cyberattacks with Trusted Image Registries Bryan Langston @LangstonBryan, Director, Cloud Architecture, Mirantis
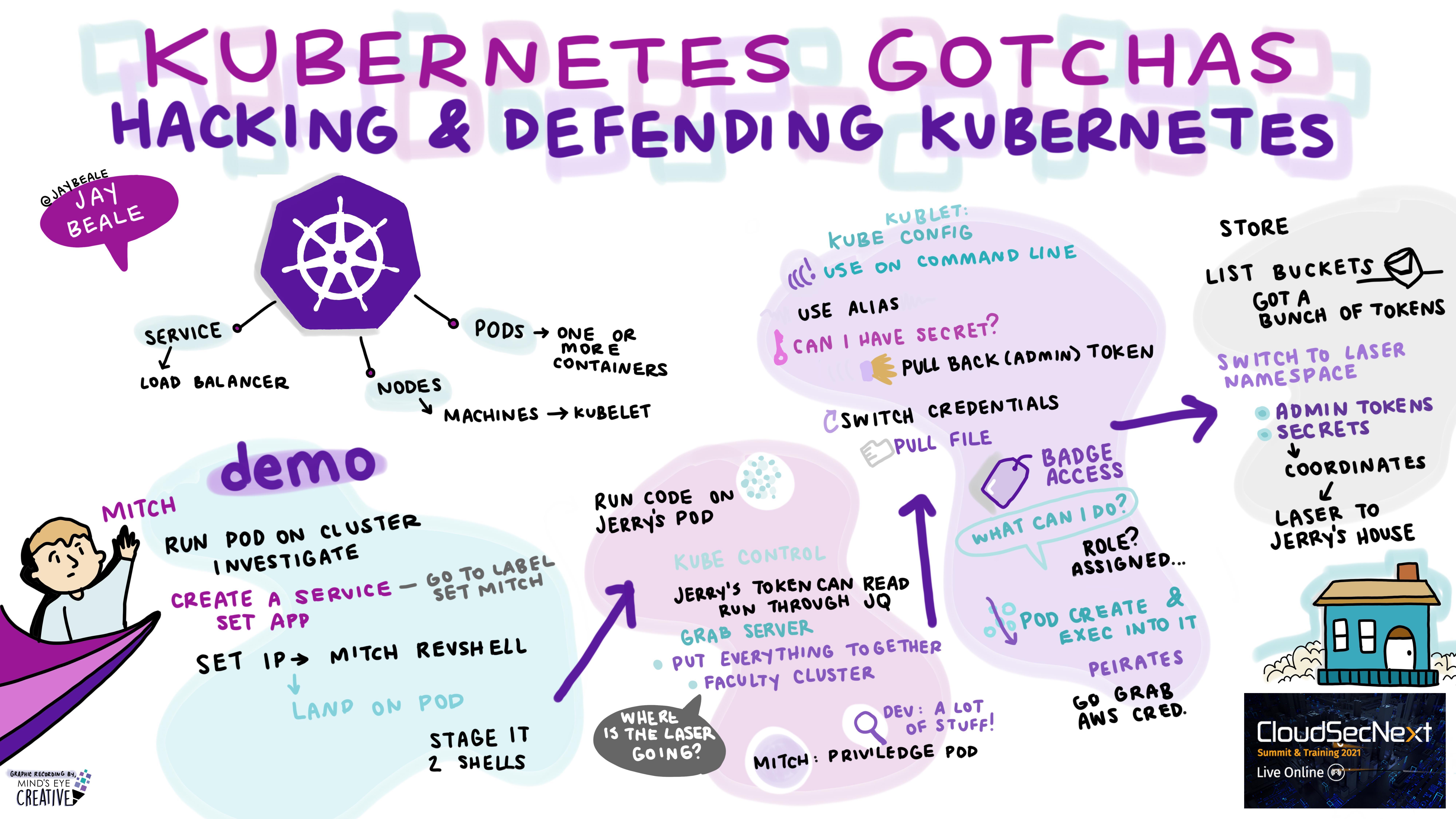
Kubernetes Gotchas – Hacking and Defending Kubernetes Jay Beale @jaybeale, CTO, InGuardians
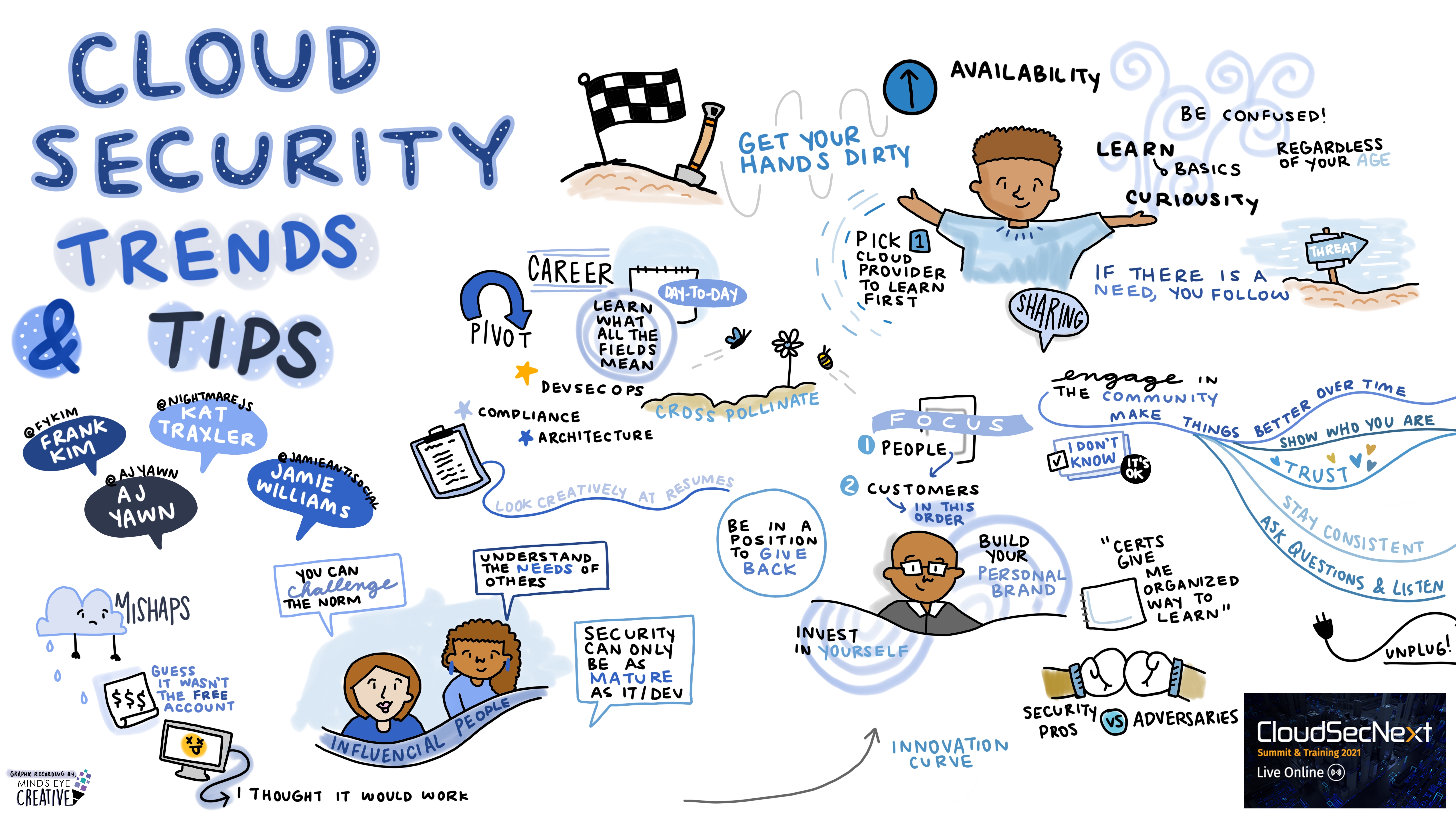
Expert Panel: Cloud Security Trends and Tips Moderator: Frank Kim @fykim, Fellow, SANS Institute Panelists: AJ Yawn @AjYawn, Co-Founder and CEO, ByteChek Kat Traxler @NightmareJS, Cloud Security Engineering, Best Buy Jamie Williams @jamieantisocial, Lead Cyber Adversarial Engineer, The MITRE Corporation
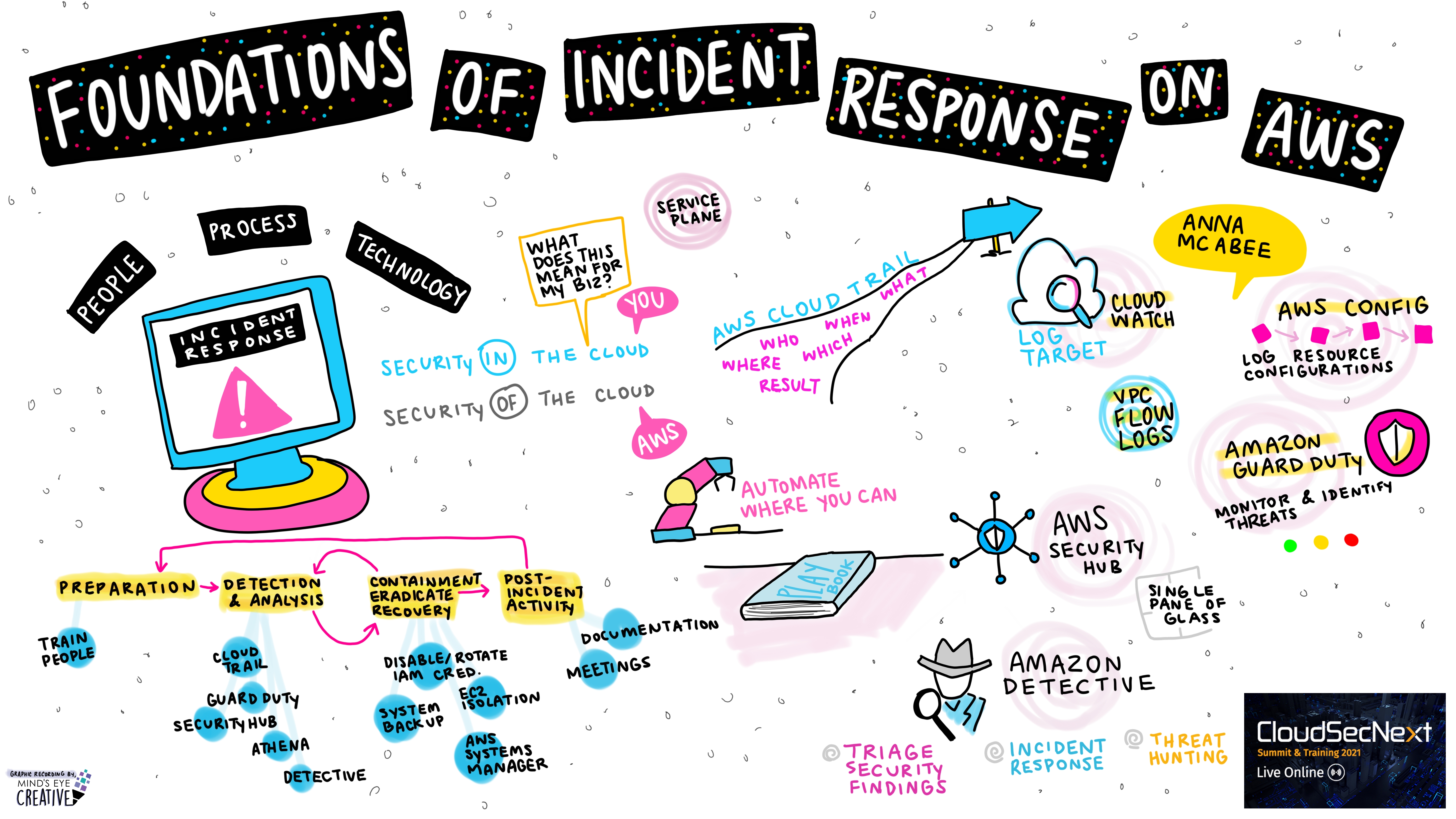
Foundations of Incident Response on AWS Anna McAbee, Solutions Architect, Security at Amazon Web Services (AWS)
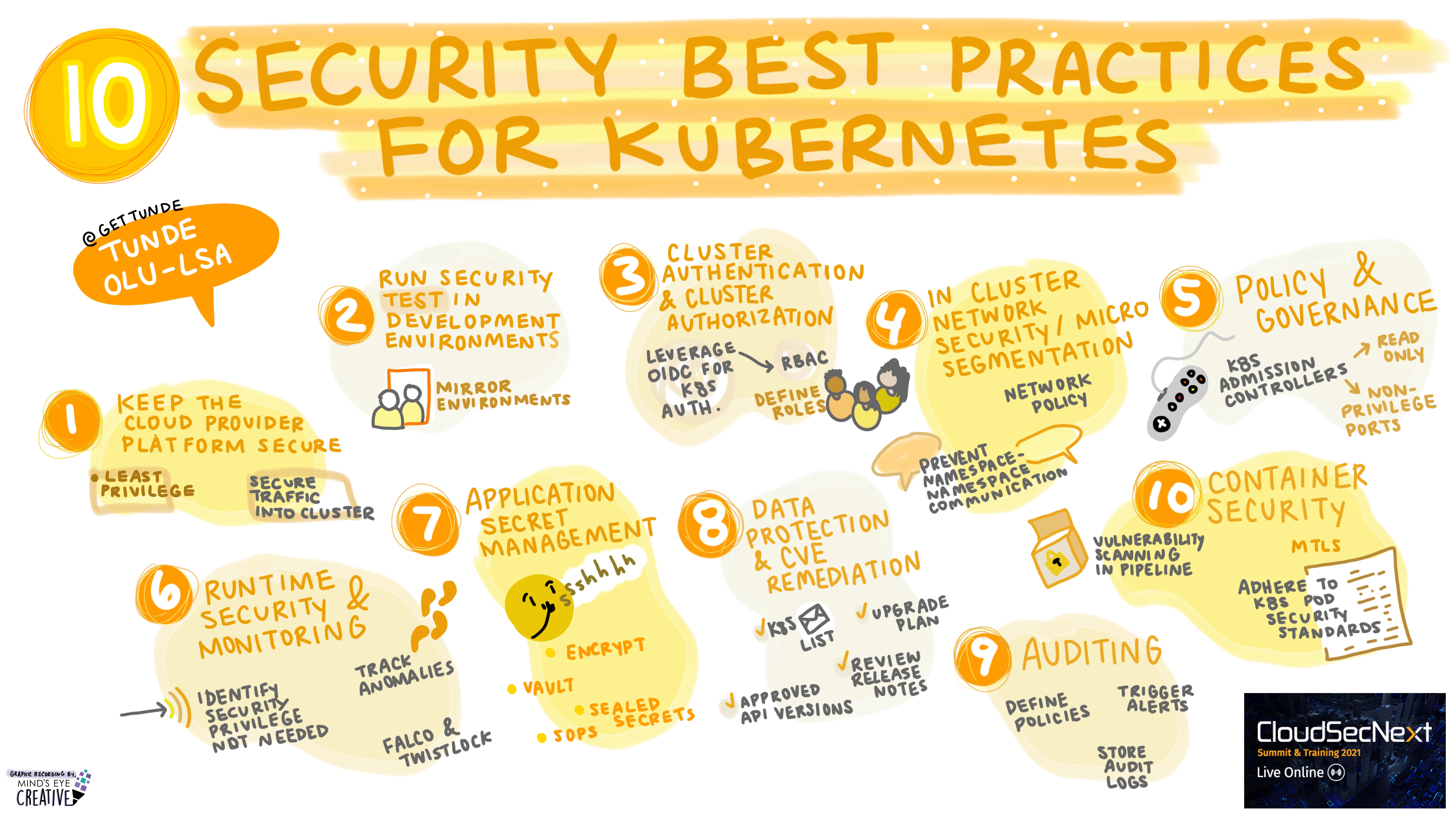
10 Security Best Practices for Kubernetes Tunde Olu-Isa @getTunde, Managing Consultant (Software Engineer), Oteemo
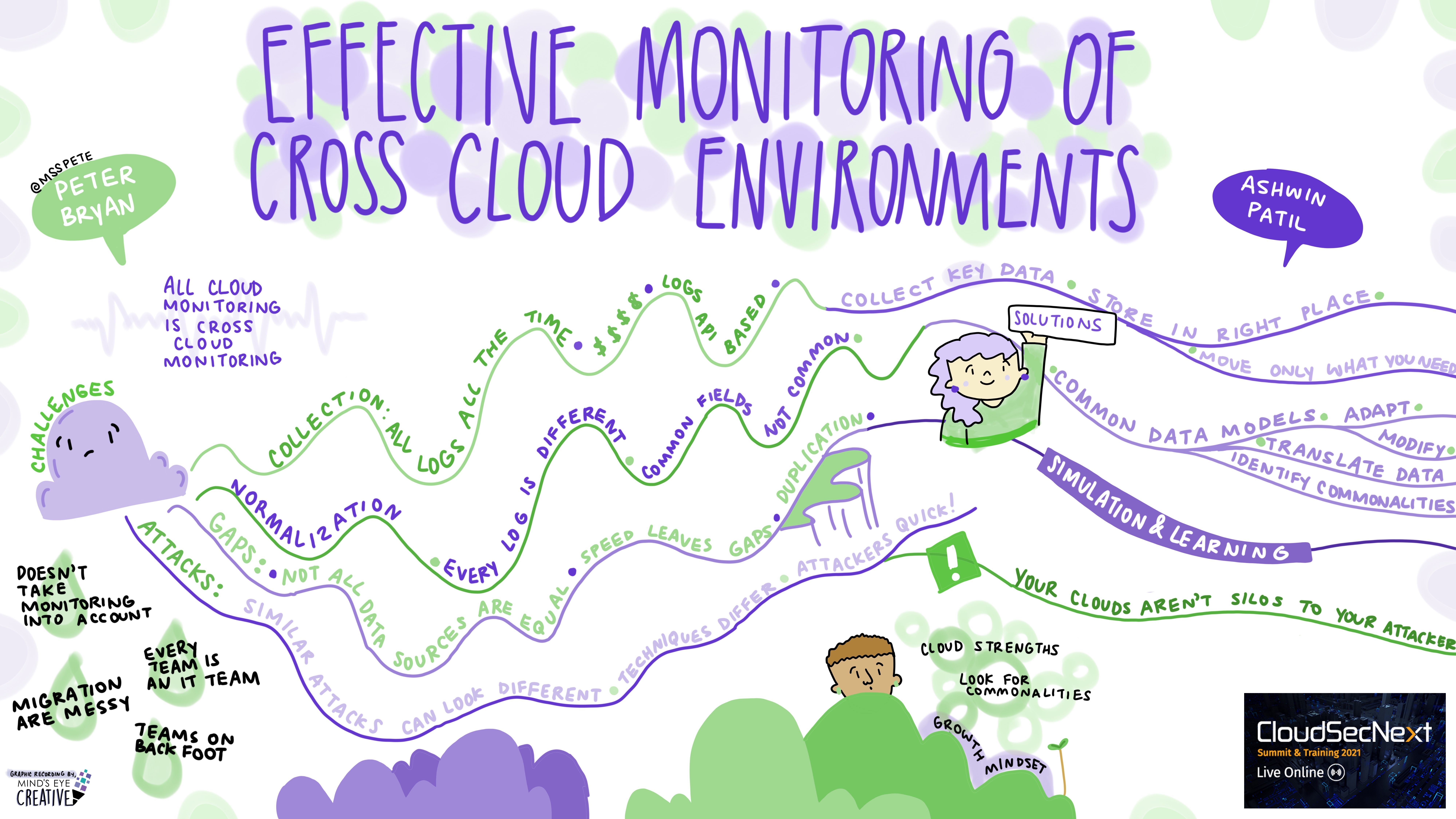
Effective Monitoring of Cross Cloud Environments Peter Bryan @MSSPete, Senior Software Engineer, Microsoft Threat Intelligence Center Ashwin Patil, Senior Program Manager, Microsoft Threat Intelligence Center
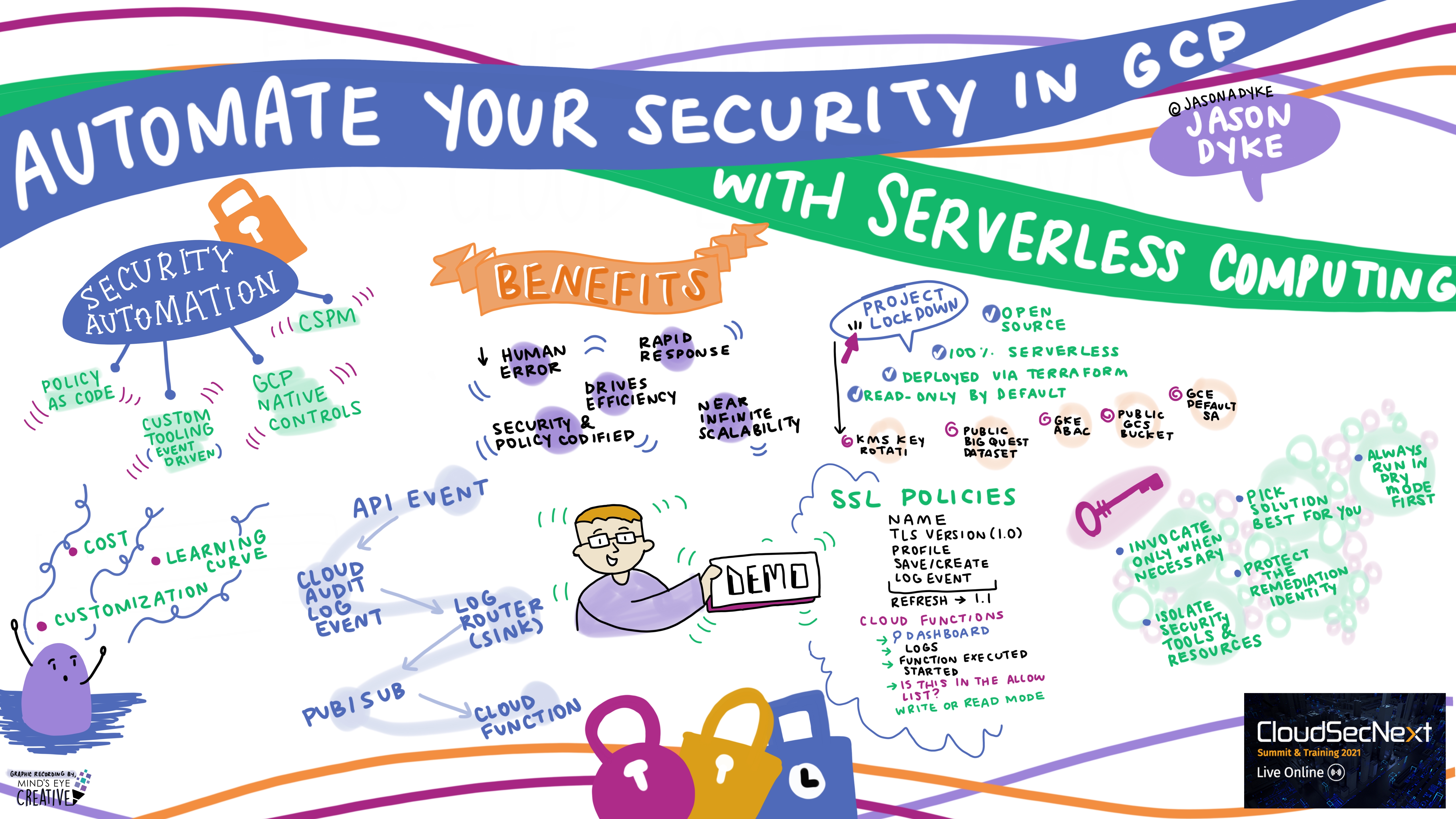
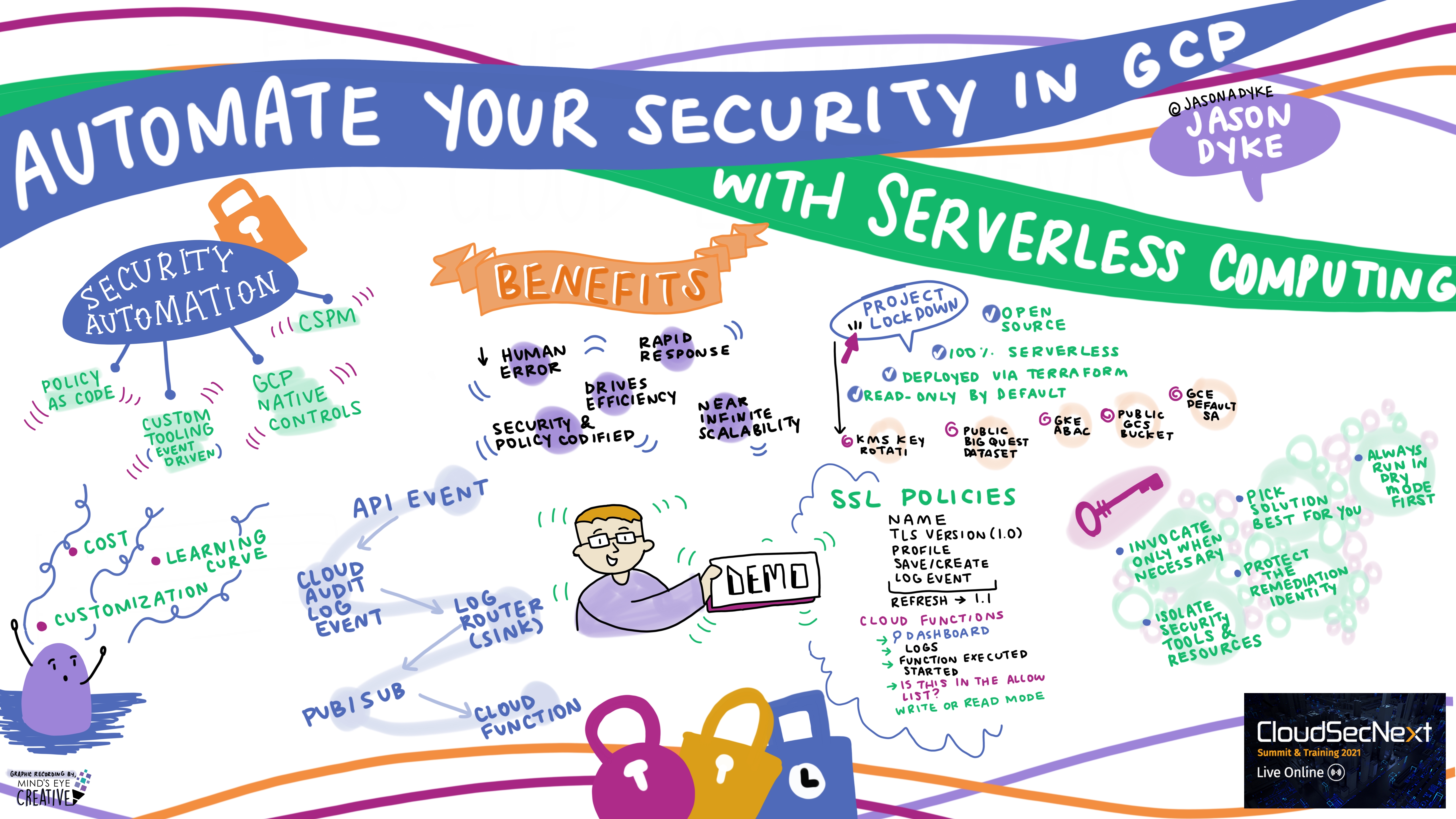
Automate Your Security in GCP with Serverless Computing Jason Dyke @jasonadyke, Principal Cloud Security Consultant, ScaleSec
Did you attend and enjoy CloudSecNext Summit? Check out these other upcoming FREE Summits.