SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
Contact Us
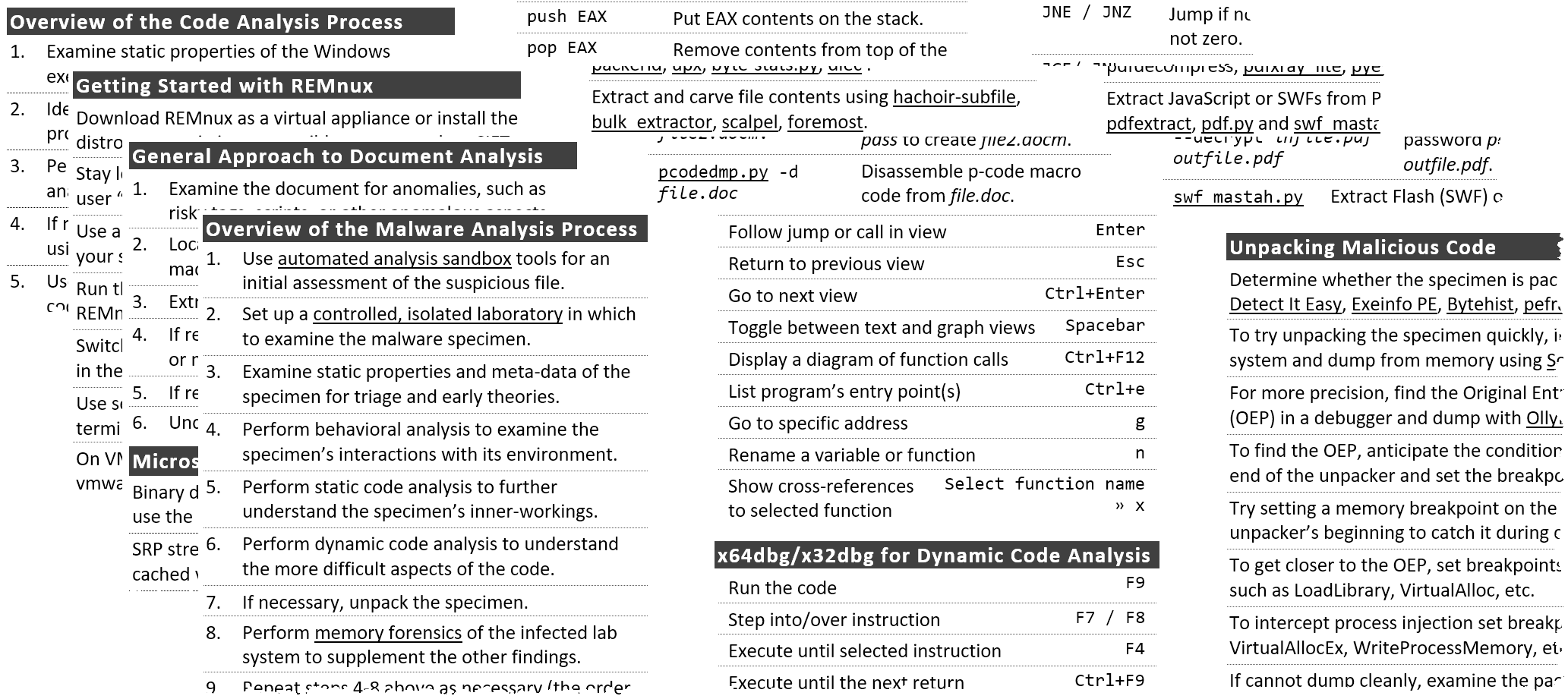
What tools can assess a suspicious RTF file? How to deobfuscate a JavaScript attachment? Where to set breakpoints for unpacking a malicious executable? What utilities can intercept C2 traffic in the lab? How do the various reverse-engineering methods fit together?
So much to remember! I created 4 cheat sheets to make it easier to recall answers to these and many other malware analysis questions.
Some of these cheat sheets have been around for a while; I recently updated them to reflect the latest tools and techniques. The one listed first is brand new:
I placed a 1-page limit on each of these cheat sheets to force myself to be selective and succinct. As a result, their contents are quite condensed. You're welcome to print PDF versions of each file or modify Microsoft Word versions for your own needs.
Many of the tools and techniques captured in these cheat sheets are covered in the FOR610: Reverse-Engineering Malware course I've co-authored at SANS.
For additional references from SANS faculty members, see the Community: Cheat Sheets page on the SANS Digital Forensics and Incident Response site.
-- Lenny Zeltser
Lenny Zeltser is a Faculty Fellow at SANS Institute. He is active on Twitter.


Lenny Zeltser, CISO at Axonius, is a leader in developing resilient security programs. His invaluable tools, like REMnux, a widely used Linux distribution for malware analysis, have become industry standards in combating malicious software.
Read more about Lenny Zeltser