SEC504: Hacker Tools, Techniques, and Incident Handling


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usConnect, learn, and share with other cybersecurity professionals
Engage, challenge, and network with fellow CISOs in this exclusive community of security leaders
Become a member for instant access to our free resources.
Sign UpMission-focused cybersecurity training for government, defense, and education
Explore industry-specific programming and customized training solutions
Sponsor a SANS event or research paper
We're here to help.
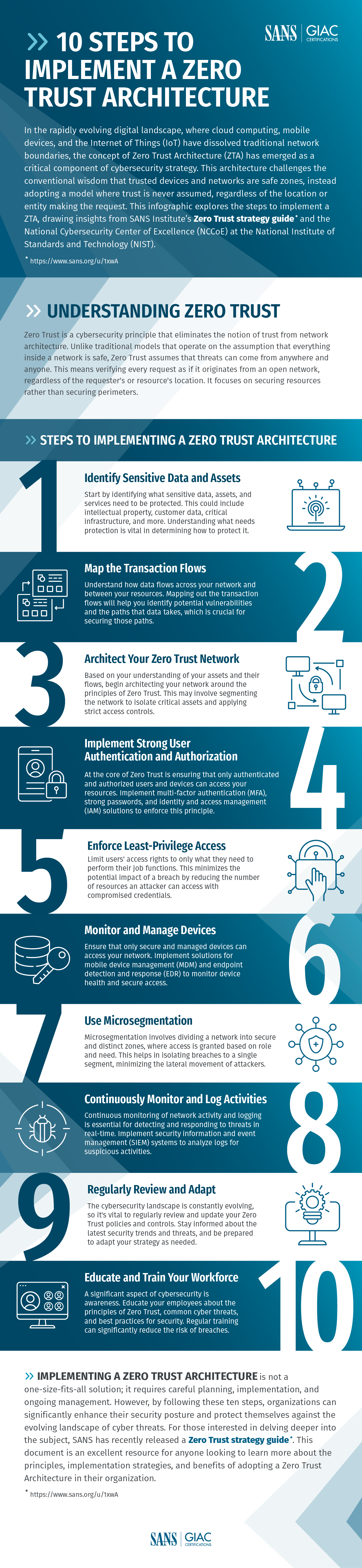
Contact UsThis infographic outlines ten essential steps to successfully implement a Zero Trust Architecture.

In an era where cyber threats are becoming increasingly sophisticated, traditional security models are no longer sufficient to protect sensitive data and critical assets. Enter Zero Trust Architecture (ZTA) — a revolutionary approach that assumes no entity, inside or outside the network, is inherently trustworthy. By continuously verifying every user and device, regardless of their location, ZTA provides a robust defense against modern cyberattacks. This infographic outlines ten essential steps to successfully implement a Zero Trust Architecture, offering practical guidance to help cybersecurity practitioners effectively adopt this model in their organizations.
Download the full white paper, authored by James Lyne, for all the details on these top cybersecurity trends.
To download your own copy of the below infographic with embedded links, click here.
Download the full white paper, authored by James Lyne, for all the details on these top cybersecurity trends.
To download your own copy of the above infographic with embedded links, click here.


Launched in 1989 as a cooperative for information security thought leadership, it is SANS’ ongoing mission to empower cyber security professionals with the practical skills and knowledge they need to make our world a safer place.
Read more about SANS Institute